Zentyal Configuration¶
This page will cover the configuration of the Zentyal server to act as a mail and file sharing server.
Objectives¶
The objectives that will be accomplished are:
- (Optional) Uninstallation of Snap.
- (Optional) Additional configuration of local system users:
- Modification of the prompt.
- Modifications to the history.
- Configuration for the vim editor.
- Creation of a SWAP partition.
- Configuration of additional EBS volumes.
- Implementation of quotas in the file system.
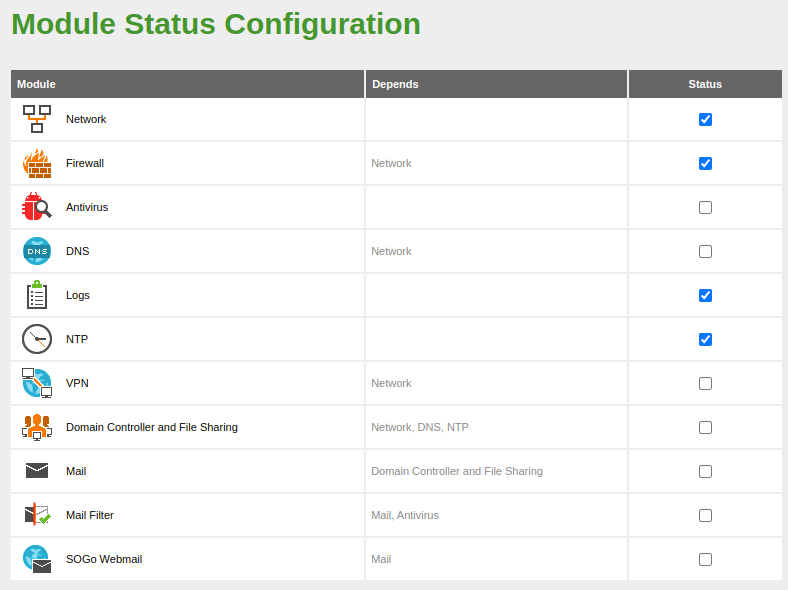
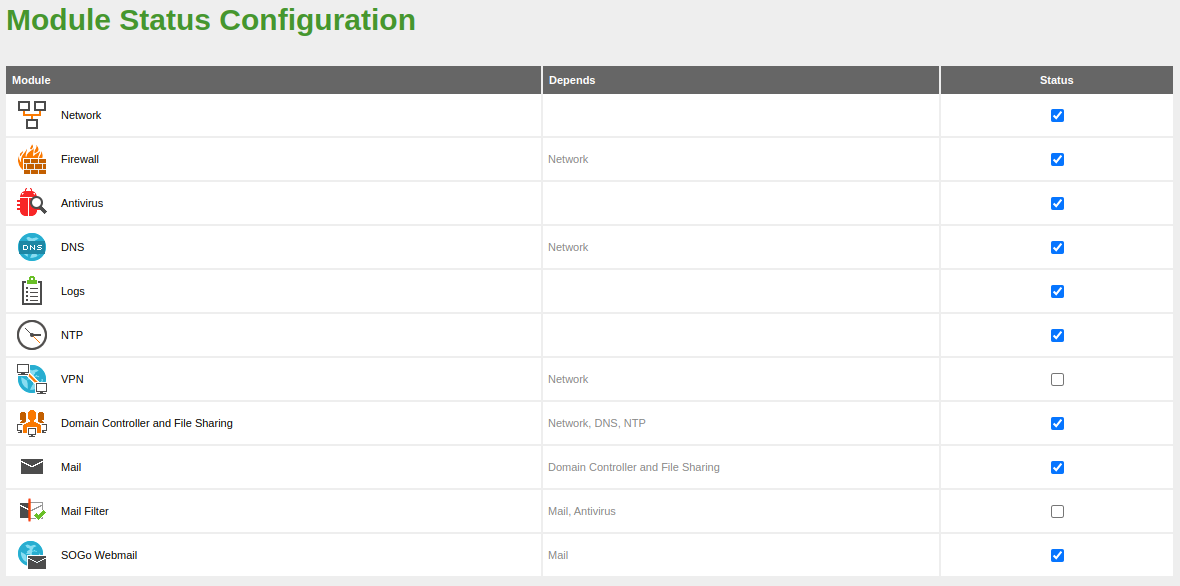
- Configuration of the following Zentyal modules:
At the end of this document, the Zentyal server will be ready to use, although in subsequent documents we will continue to establish additional configurations such as the configuration of Let's Encrypt issued certificates or highly recommended options such as hardening of the mail service.
Optional Configuration¶
In this section, various optional configurations will be made on the Zentyal server, so it can be skipped and move on to the 'Previous Configuration' section. Snap
Since Zentyal does not use Snap, we will proceed with its uninstallation.
-
Stop the service:
-
Remove the package:
-
Remove the directories that remain in the file system:
Prompt¶
To improve the user experience when performing tasks from the CLI, we will enable prompt colors for existing and future local users.
History¶
In order to store more information in the personal history of users and also have a timestamp indicating the date and time a certain command was executed, we will add a series of additional options to both existing and future local users.
Vim¶
We will add a simple custom configuration for the vim text editor for both existing and future users. This configuration will establish the following:
- Tabulation of 2 spaces.
- Enables syntax highlighting.
- Displays line numbers.
- Uses the 'desert' color scheme.
- Configures the editor to use Yaml files.
To set up the configuration, simply create a file called .vimrc in the users' home directory.
Previous Configuration
Previous Configuration¶
The previous configurations will be made before configuring the Zentyal modules. Except for the Additional EBS Volumes section, which is optional, the rest should be implemented.
SWAP Partition¶
It is highly recommended to configure a SWAP partition on the server to increase server availability in case of RAM-related spikes. The actions we will take are documented here.
-
Create an empty 4GB file, which will be the size of our SWAP partition:
-
Set the permissions for the file:
-
Set the file as a SWAP area:
-
Enable the SWAP partition temporarily:
-
Verify that the system recognizes the new SWAP partition by running the following commands:
The result we should get is:
-
Set the partition in the /etc/fstab configuration file so that it persists after the server restarts:
-
Finally, check that the new entry in the file does not contain syntax errors:
Additional EBS volumes¶
In case we have added additional EBS volumes - as in my case for mailboxes and shared resources -, we will proceed to configure and mount them on the server.
Note
For the mount point of shared resources, /home/samba/ could be used instead of /home/. However, using /home/samba/ the personal directories of domain users (shared in 'H' letter by default) would not be stored in the EBS volume.
-
List the volumes with the command:
In my specific case, it shows the following result:
-
Create a single partition that occupies the entire disk on the nvme1n1 and nvme2n1 volumes:
Info
'8e' sets the partition label as 'Linux'.
-
Verify that the partitions have been created correctly:
In my specific case, it shows the following result:
-
Set ext4 as the file system for the new partitions:
-
Verify that everything went well with the command:
In my specific case, it shows the following result:
-
Create the directory where the EBS volume for mailboxes will be mounted:
-
Temporarily mount the EBS volume that will contain the shared resources:
-
Copy the content of the /home/ directory to the temporary directory where we have mounted the EBS volume:
-
Unmount the EBS volume:
-
Obtain the identifier (UUID) of the volumes:
In my specific case, it shows the following result:
Warning
Remember that the volume for mailboxes was mounted first, so its mount point is
/dev/nvme1n1p1. -
Set the EBS volume mounting in the
/etc/fstabfile:Warning
You will have to change the value of the
UUIDparameter to your value obtained in step 7. -
Mount the volumes to verify that there are no syntax errors in the file from the previous step:
-
Finally, confirm that they have been mounted correctly by running the following commands:
In my specific case, it shows the following result:
Quota¶
To be able to use the quotas that Zentyal allows setting to limit the use of information that a domain user can store on the server, as well as for the maximum mailbox size, it is necessary to install a series of packages and enable their use on the disk.
Note
It is not necessary to enable the quota on the disk that contains the mailboxes, since Zentyal manages them differently.
-
Install the following packages required for AWS instances:
-
Set the additional mount options on the EBS volume for shared resources, to do this, edit the configuration file /etc/fstab:
Info
The added options are:
usrjquota,grpjquota, andjqfmt. -
Restart the server so that the latest kernel is loaded and we can securely enable quotas:
-
Add the Quota module to the kernel:
-
Persist the previous change:
-
Let the system check quotas and create the necessary files:
The result I obtained in my case was:
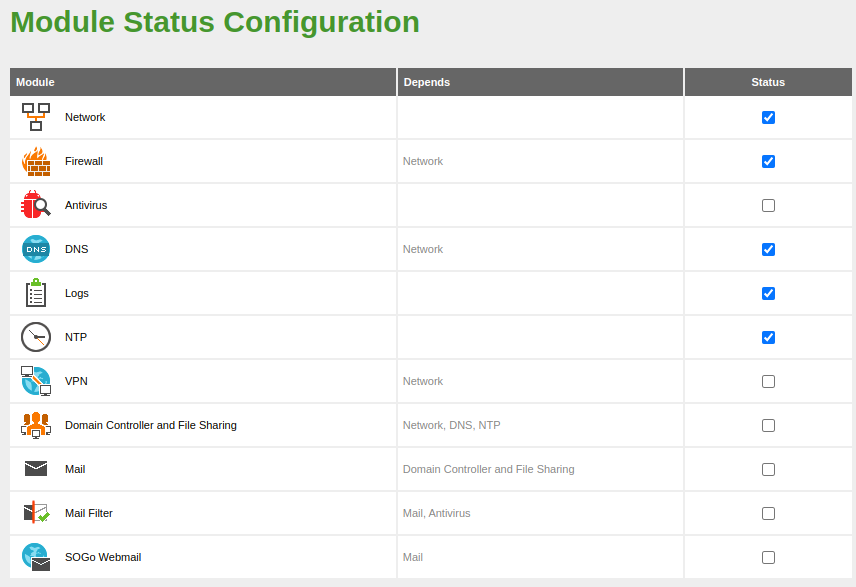
Configuration of the modules¶
From this point on, we will be able to install, configure and check the Zentyal modules.
General¶
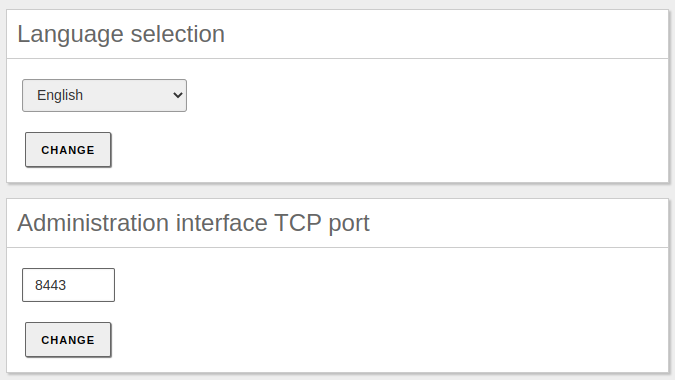
First of all, what we need to do is configure the Zentyal base from the System -> General menu.
-
We will set the language of the administration panel and the port on which the webadmin module will listen:
-
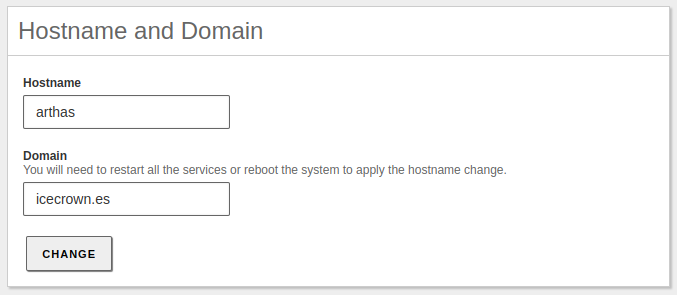
Then, from the same panel, we set the server name and domain:
Warning
Once we enable the domain controller module, these 2 values cannot be changed.
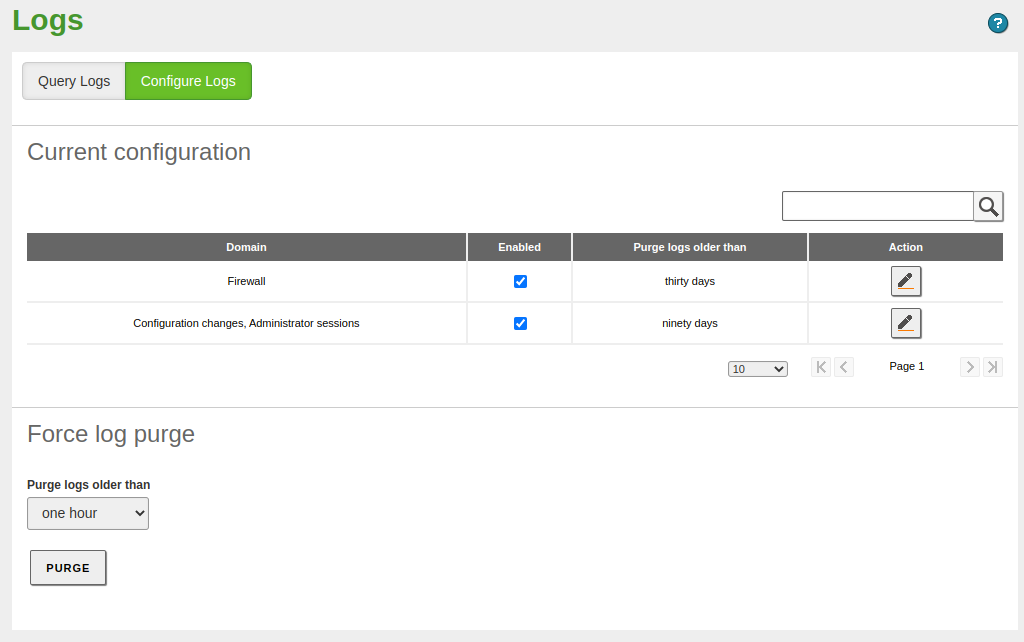
Logs module¶
Initially, we will enable the available 'domains', change the retention time to 30 days for the firewall and 90 for the administration panel changes as well as administrator logins:
Firewall module¶
For our network configuration (internal) and the modules we will use, the firewall sections we will use are:
- Filtering rules from internal networks to Zentyal
- Filtering rules from traffic coming out from Zentyal
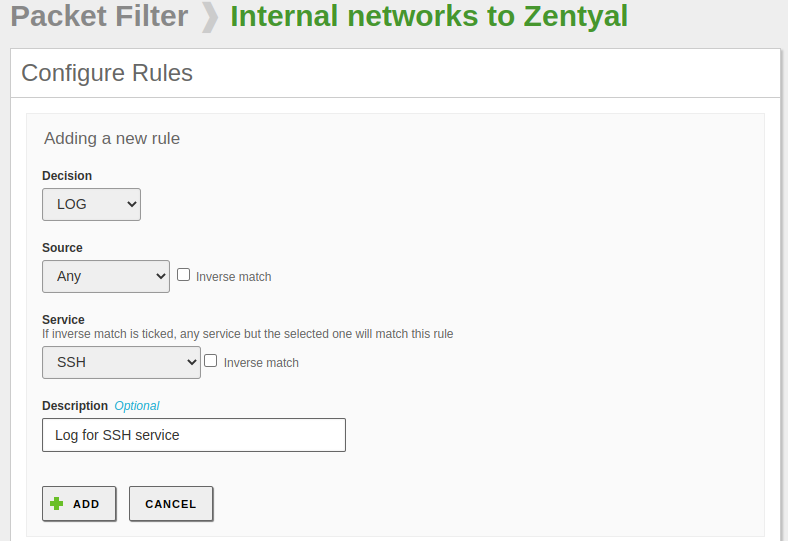
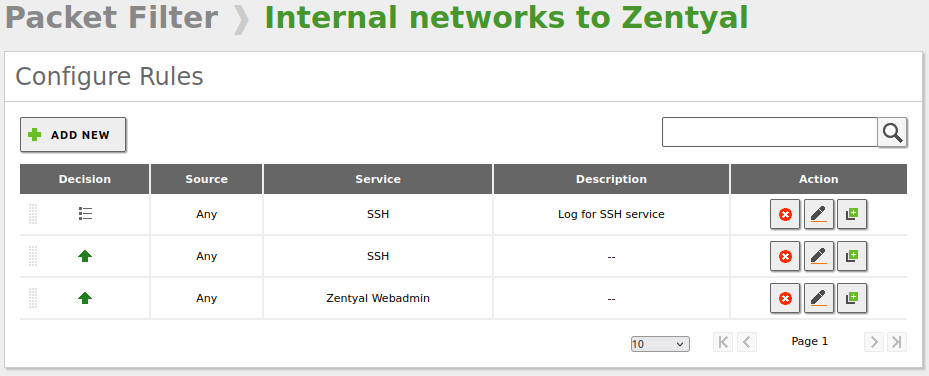
The default policies in both firewall sections are secure; however, we will add a LOG rule for SSH connections as it is always a good idea to have as much information as possible about this critical service. To do this, we will go to Firewall -> Packet Filter -> Filtering rules from internal networks to Zentyal and add the following rule:
Resulting in the following rules:
Considerations:
- It is important that the new rule goes above the rule that accepts the SSH connection; otherwise, it will never be executed as when a rule is fulfilled, the rest are not analyzed.
- Remember that in addition to this firewall, we also have the one from AWS (Security Group associated with the instance), so we will have to make sure that both firewalls have the same rules.
- It could be configured in the Zentyal firewall to allow all traffic and then, from the security group, be more restrictive, or vice versa. However, it is recommended to configure both equally.
Software module¶
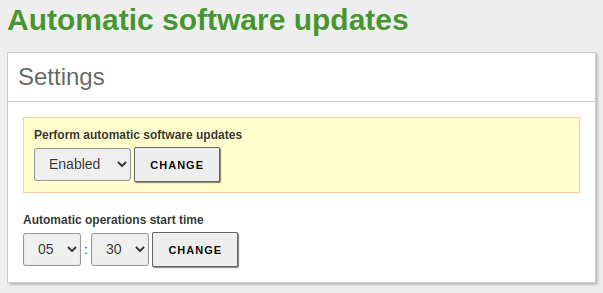
In order to have our server updated, we will enable and set the time at which automatic updates will be installed. In addition, we will proceed to install the modules we are going to use.
-
From the
Software Management -> Settingsmenu, we set the automatic update configurations:Nota
It is highly recommended to set a time that is after the server backups such as snapshots, so we have a stable restoration point in case an update causes a critical incident.
-
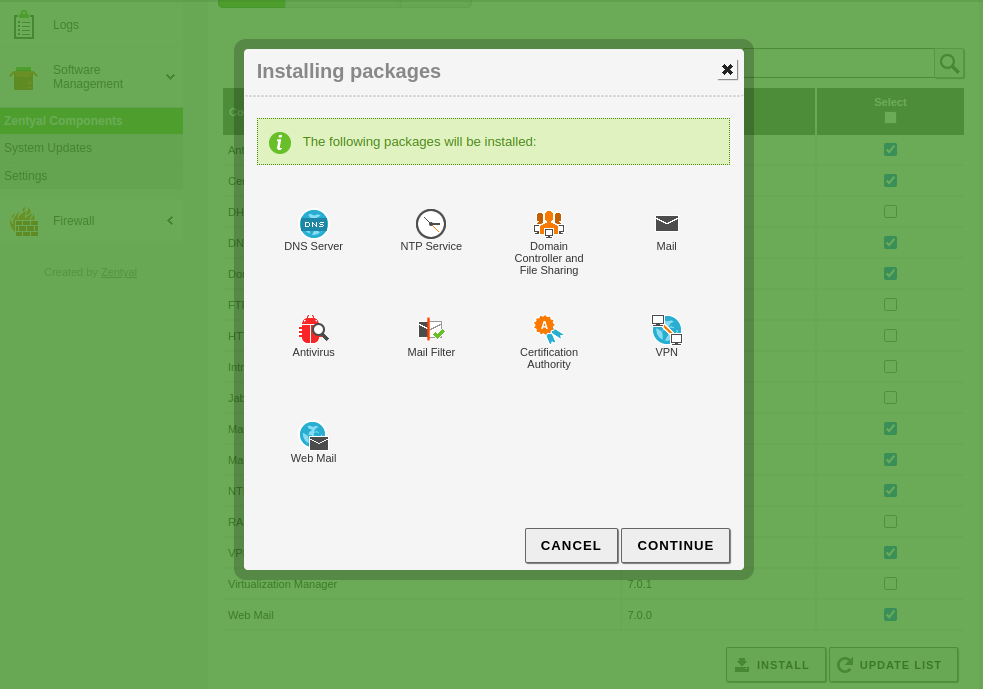
Then, from the
Software Management -> Zentyal Componentsmenu, we will proceed to install only the modules we are going to use:Info
After the modules are installed, multiple rules will be automatically created in the
Filtering rules from internal networks to Zentyalsection of the firewall to allow access to these modules.
NTP module¶
The first of the newly installed modules that we are going to configure is NTP. We will set the time zone and the geographically
-
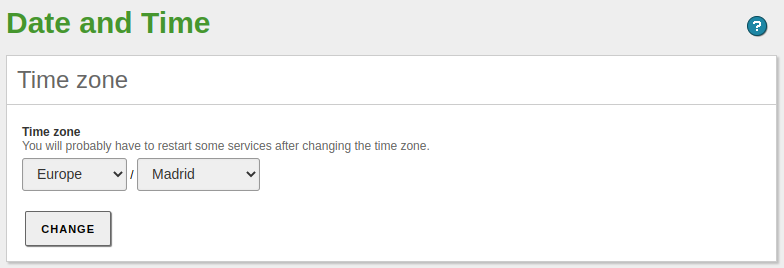
Let's go to
System -> Date/Timeand set the time zone: -
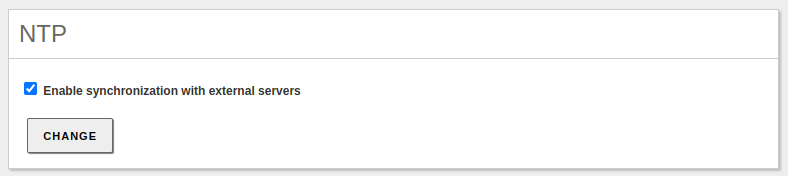
Enable the option that allows syncing time with external servers:
-
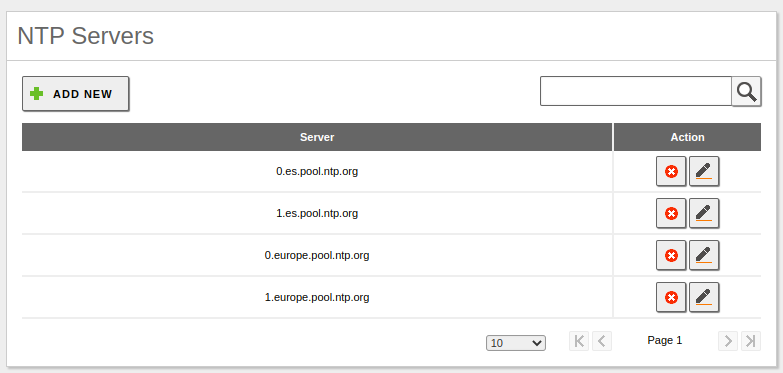
Modify the default NTP servers to the official ones we have available on this website:
-
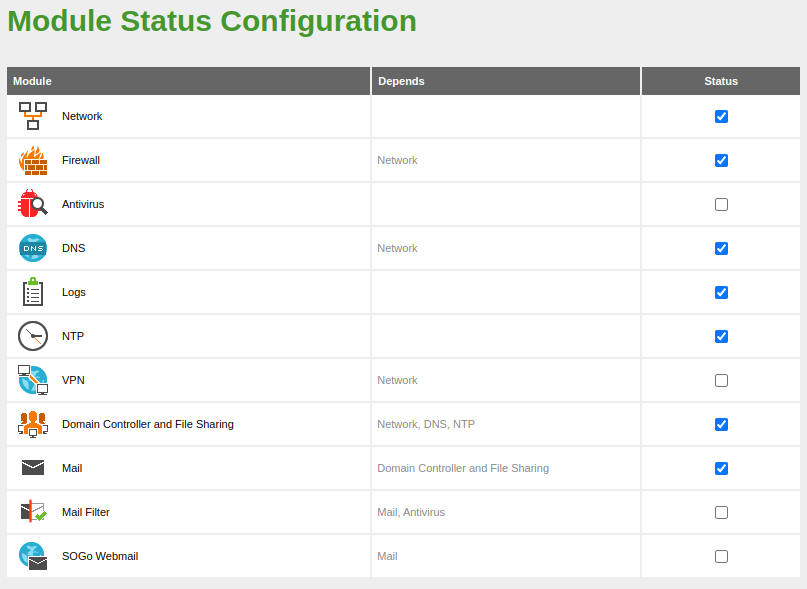
Finalmente, habilitamos el módulo de NTP desde
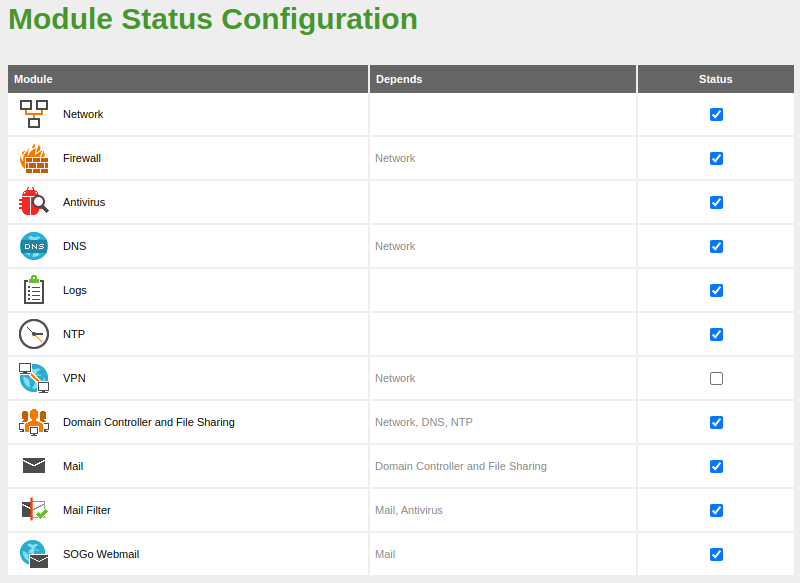
Modules Status:
DNS module¶
The next module we will proceed to configure is the DNS module, which is critical for the functioning of the domain controller module and, by dependency, also the mail module.
The configuration we will establish will be minimal, since we will manage the DNS record management from the administration panel where we have registered the domain - Route 53 in my case -.
-
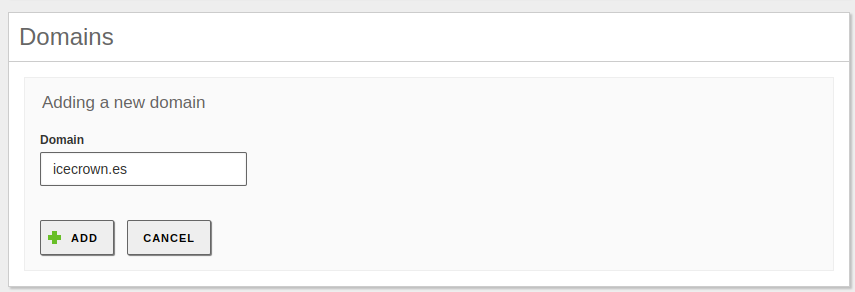
We create the domain, which must match the one created in
System -> General. To do this, from the side menu we selectDNS: -
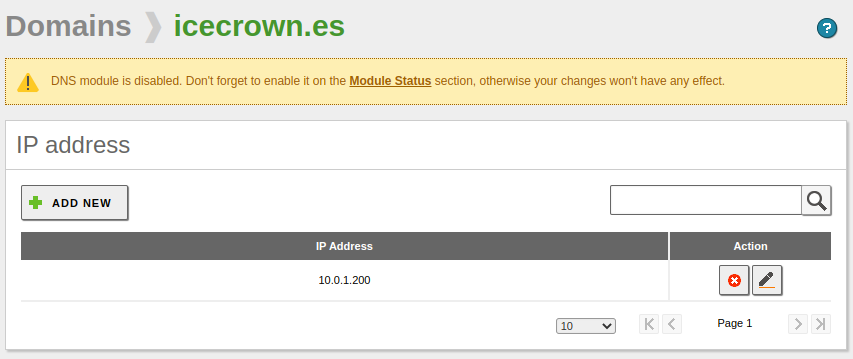
Next, we check that the server's IP address has been successfully registered to the domain, by going to the
Domain IP Addressesfield of the newly created domain: -
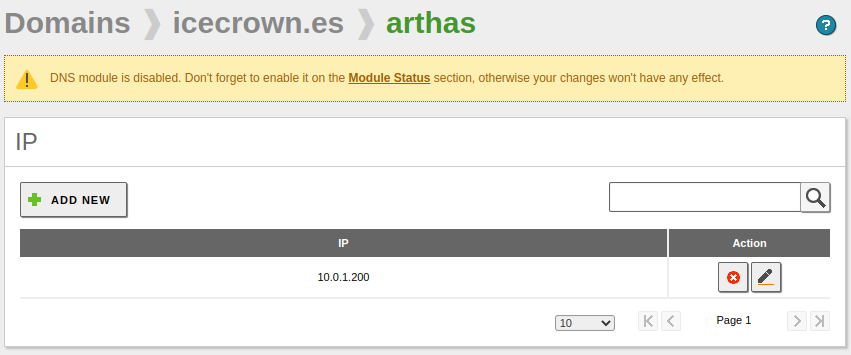
We also check that the IP has been registered for the server name. In this case, the field is
Hostnames -> IP Address: -
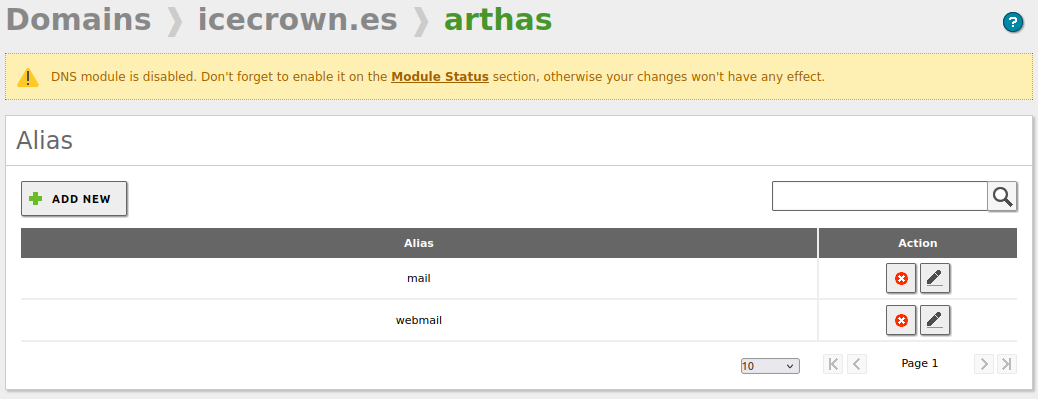
Next, we create additional alias records from
Hostnames -> Alias. In my case, I will create two records related to email: mail and webmail. -
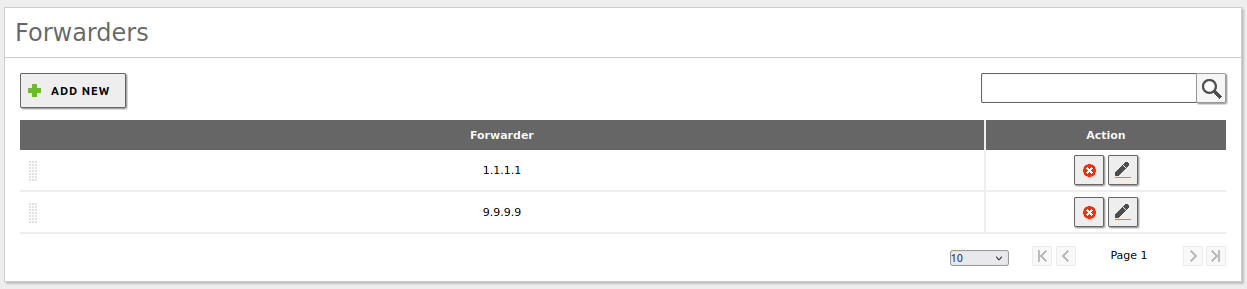
We set the DNS forwarders, which in this case will be those of Cloudflare and Quad9:
-
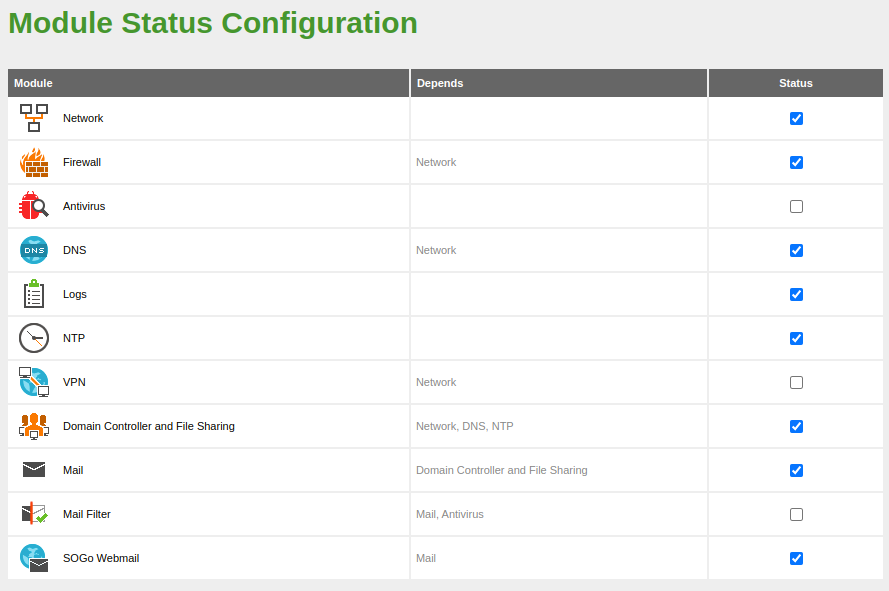
Once the module configuration has been established, we proceed to enable it from
Modules Status: -
Finally, we check that we can resolve the configured DNS records from the server itself. To do this, we will run the following commands:
Below are the results I have obtained:
As can be seen, the
statusfor all is 'NOERROR' and the 'ANSWER SECTION' shows the DNS records in question.
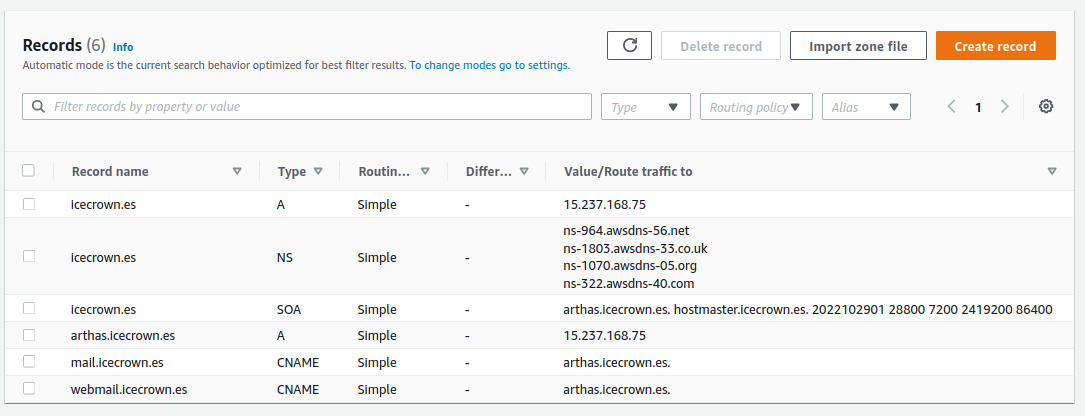
At this point, the module would be configured in Zentyal. However, we still need to create the records with the server's public IP address in the DNS provider so that they are visible externally. Here are the steps to perform for AWS Route53:
-
Go to
Route 53 -> Hosted zones -> domainand create the same records as in Zentyal but with the public IP: -
We wait a few minutes for them to replicate globally.
-
Finally, we check the resolution of the records:
A continuación, los resultados que he obtenido:
After confirming the domain's functioning both internally (from Zentyal) and externally, the DNS module will be correctly configured, and we can proceed with the next module.
Mail module¶
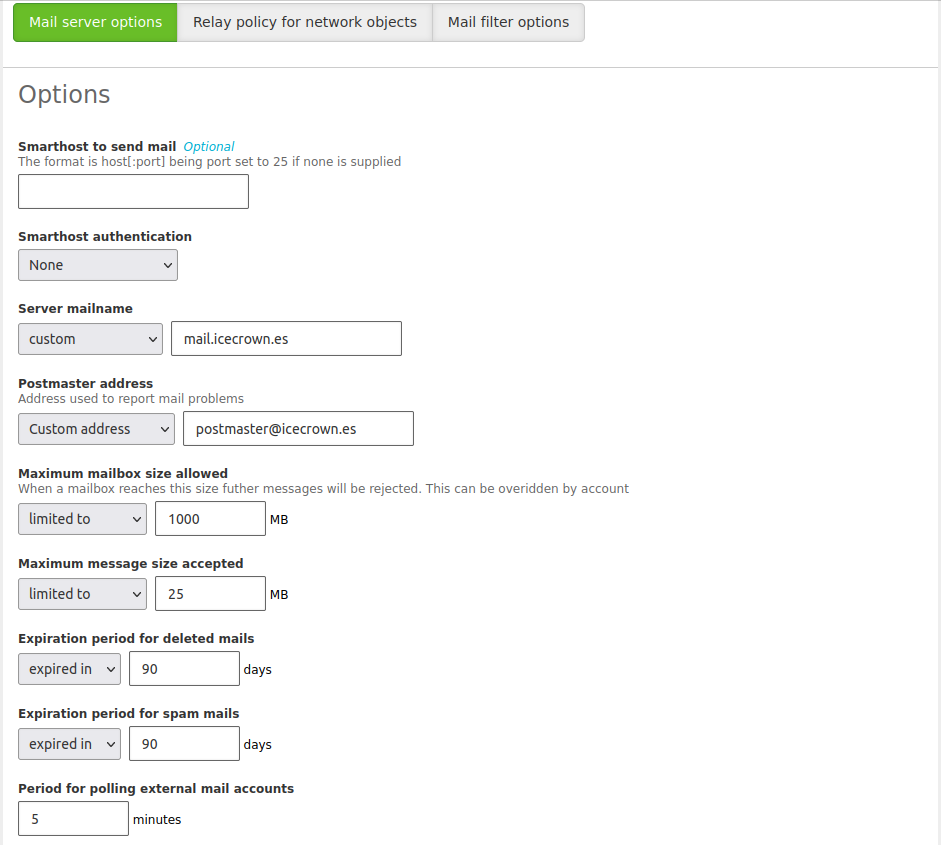
With the domain controller module configured, we can now configure the mail module, as it depends on the former to be enabled first. In my specific case, I will establish the following optional settings:
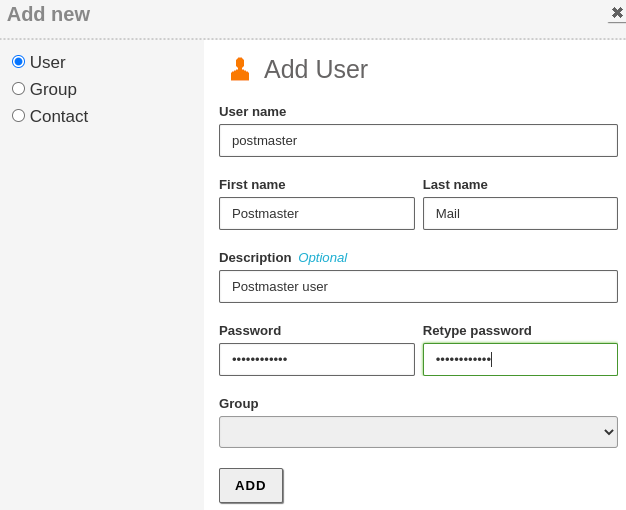
- The postmaster user will be
postmaster@icecrown.es. - I will set 1GB as the default quota for mailboxes.
- The maximum size of an accepted message will be 25MB.
- Emails deleted in mailboxes will be automatically purged after 90 days.
- Emails in the spam folder will be automatically deleted after 90 days.
- Mail account synchronization through Fetchmail will be done every 5 minutes.
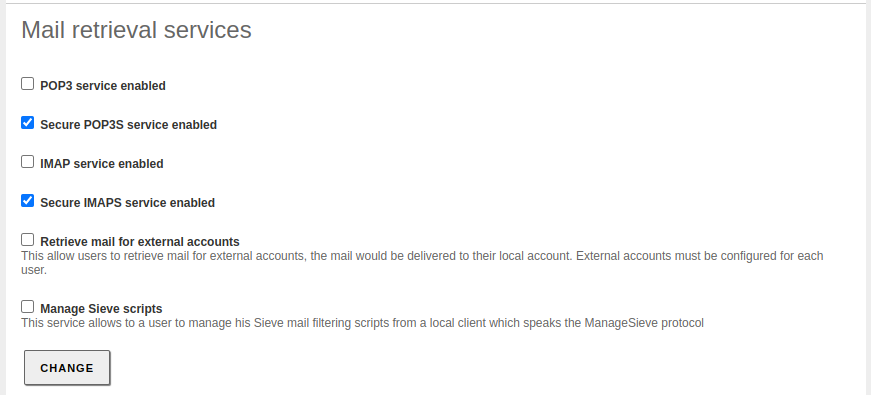
- Only IMAPS and POP3S protocols will be allowed.
- Fetchmail and Sieve will be disabled, as I won't be using them initially.
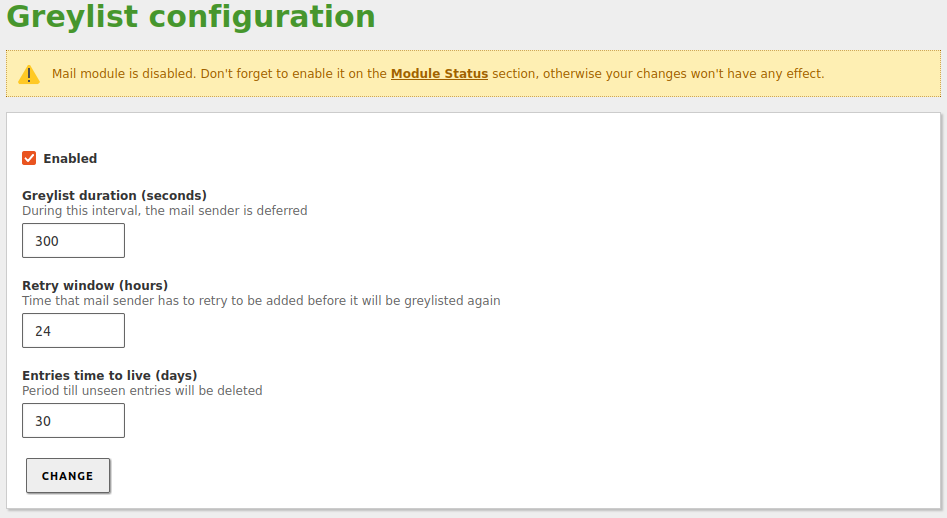
- The greylist will be enabled, and forwarding time will be reduced to 24 hours, with a 30-day deletion period.
Here are the steps to configure the module:
-
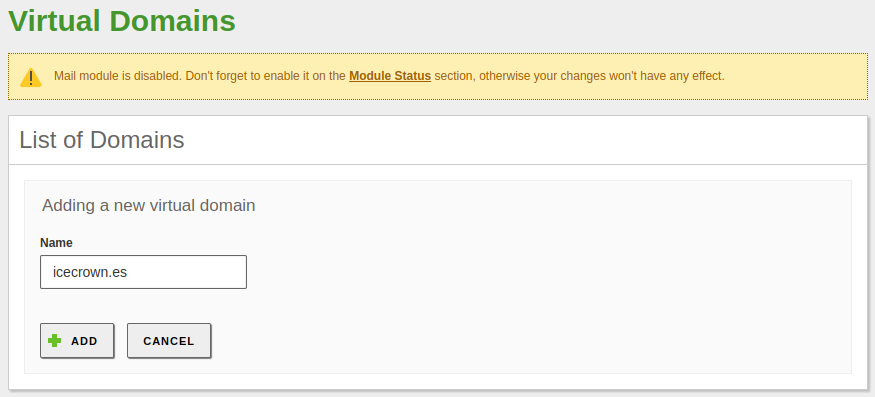
Create the virtual mail domain, which will be the same as the domain configured in the DNS module. From the left-hand side menu, go to
Mail -> Virtual Mail Domains: -
Establish the optional restrictive configurations mentioned from
Mail -> General: -
Disable Fetchmail and Sieve:
-
Enable the greylist from
Mail -> Greylist: -
Enable the module:
-
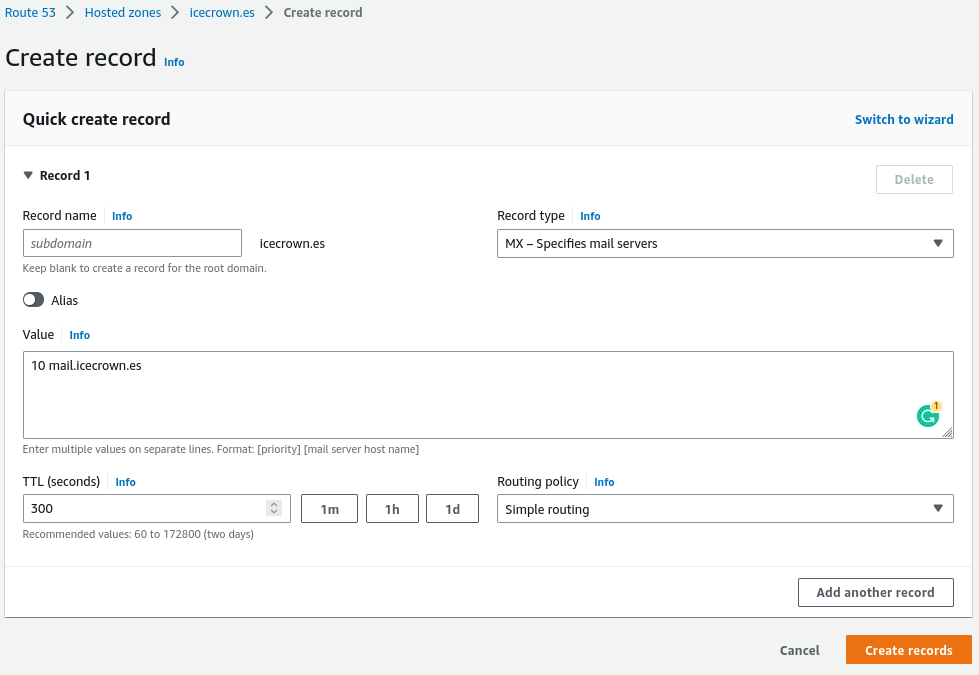
Create the
MXtype record in the domain. In my case, I will do it from Route53:Additionally, I will also create it in Zentyal, but as it is an alias, it will have to be done using the CLI:
-
Check the new DNS record both internally and externally:
The result I get is:
-
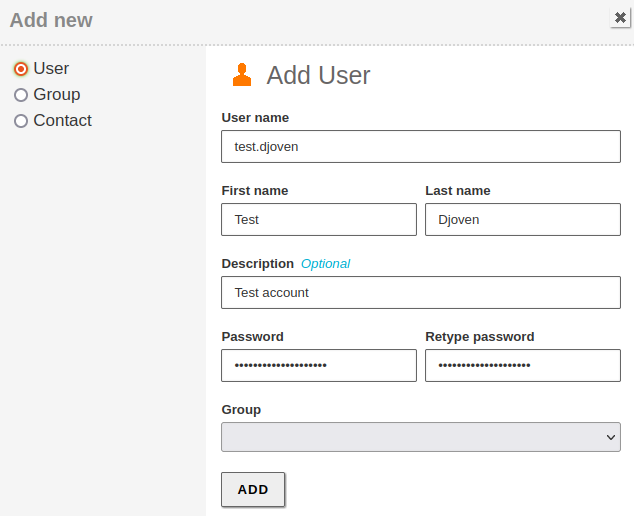
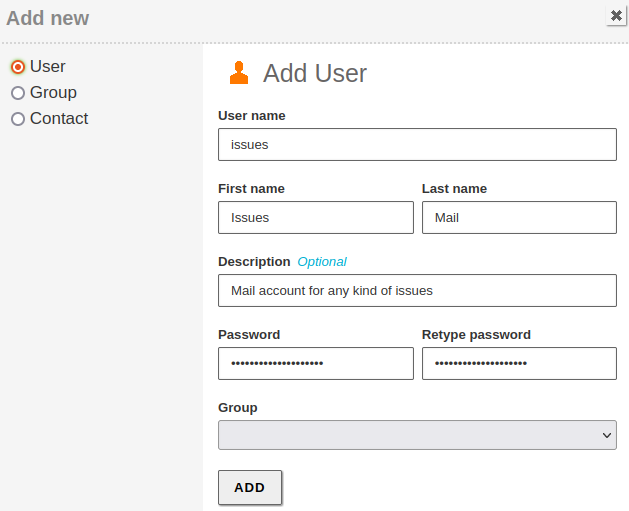
Create the
postmaster@icecrown.esuser specified in step 2 and also a test user, which in my case will be namedtest.djoven. To do this, go toUsers and Computers -> Manage:
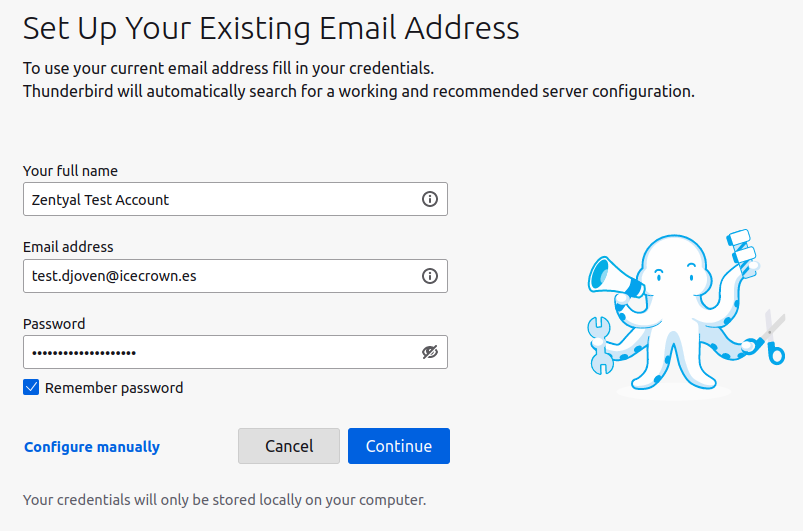
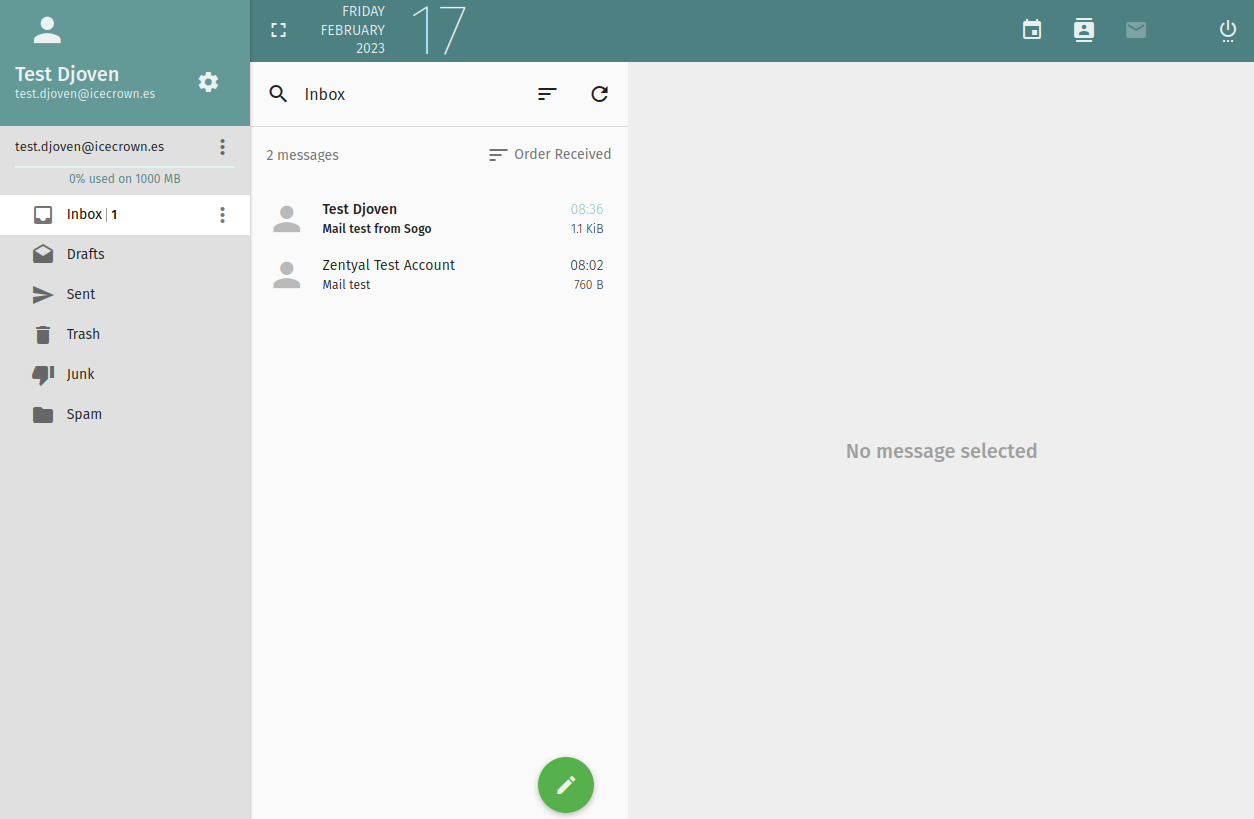
Finally, we will test with a mail client (Thunderbird in my case) that we can configure the account of the test user created:
-
Configure a new account in Thunderbird:
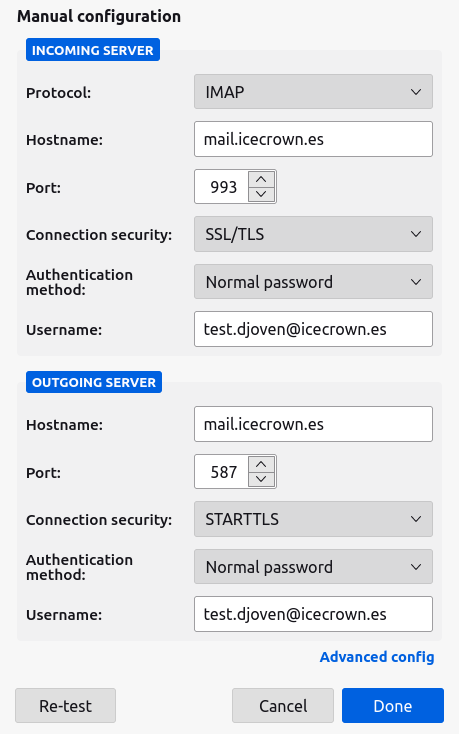
-
Set the connection data with the SMTPS and IMAPS service:
Warning
You must change the authentication type to 'Normal password', otherwise authentication will fail.
-
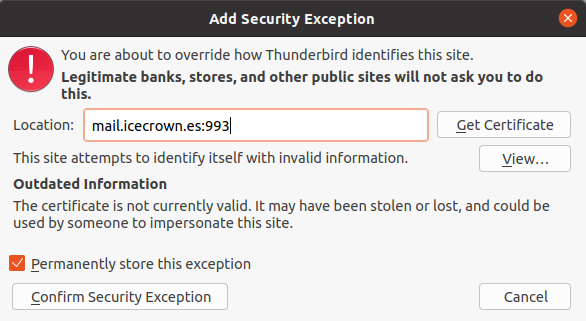
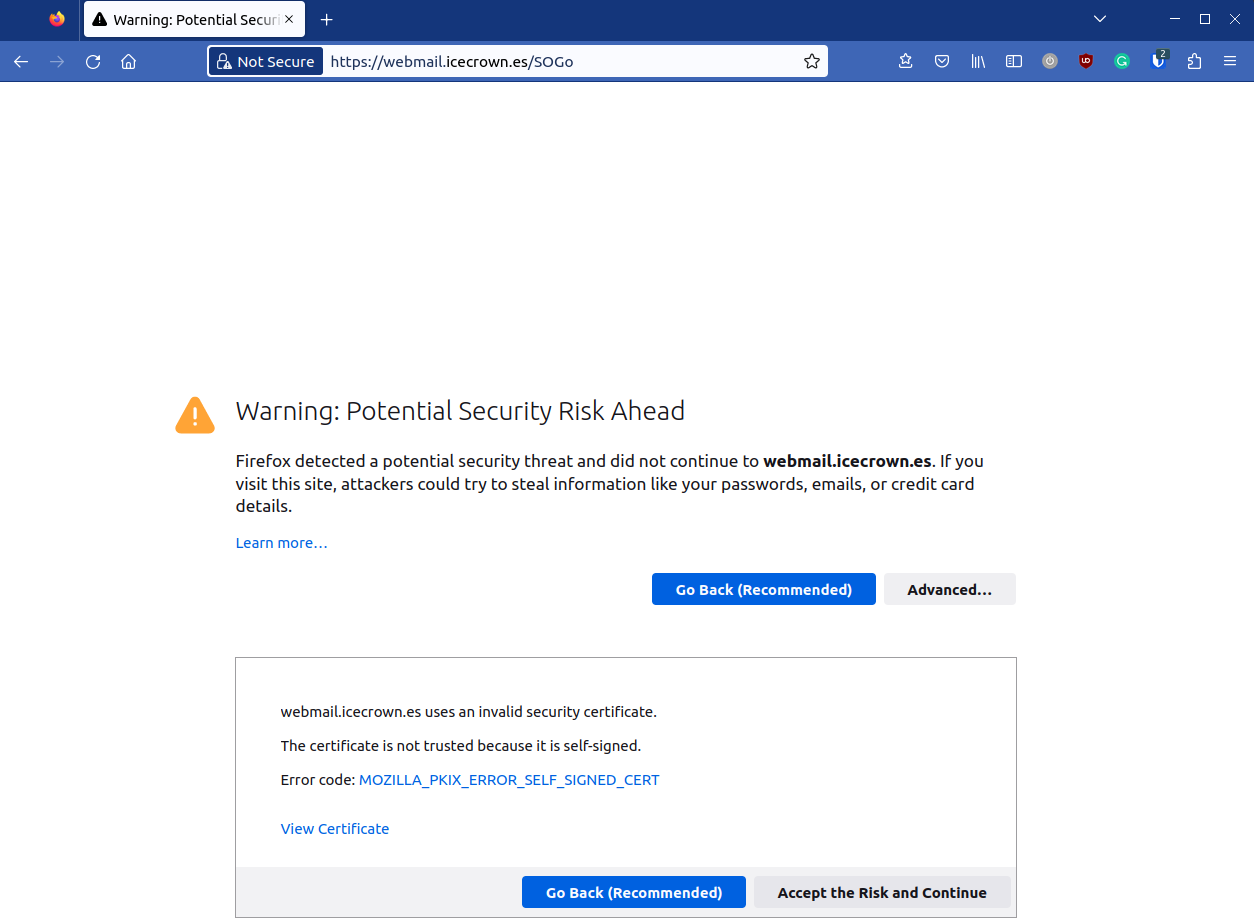
After confirming the configuration, the following warning message about the certificate will appear, which is normal, as it is a self-signed certificate by Zentyal:
-
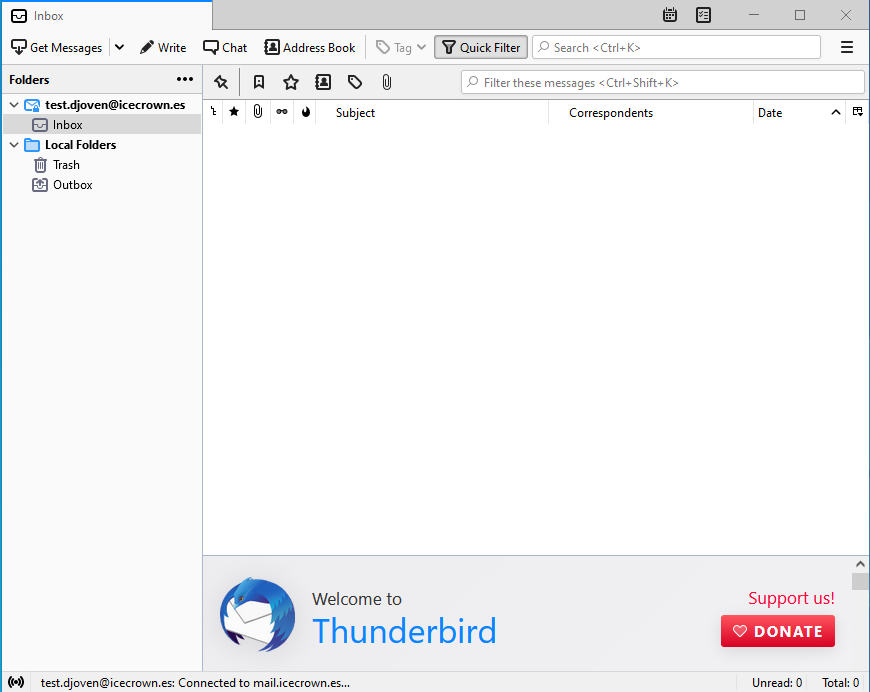
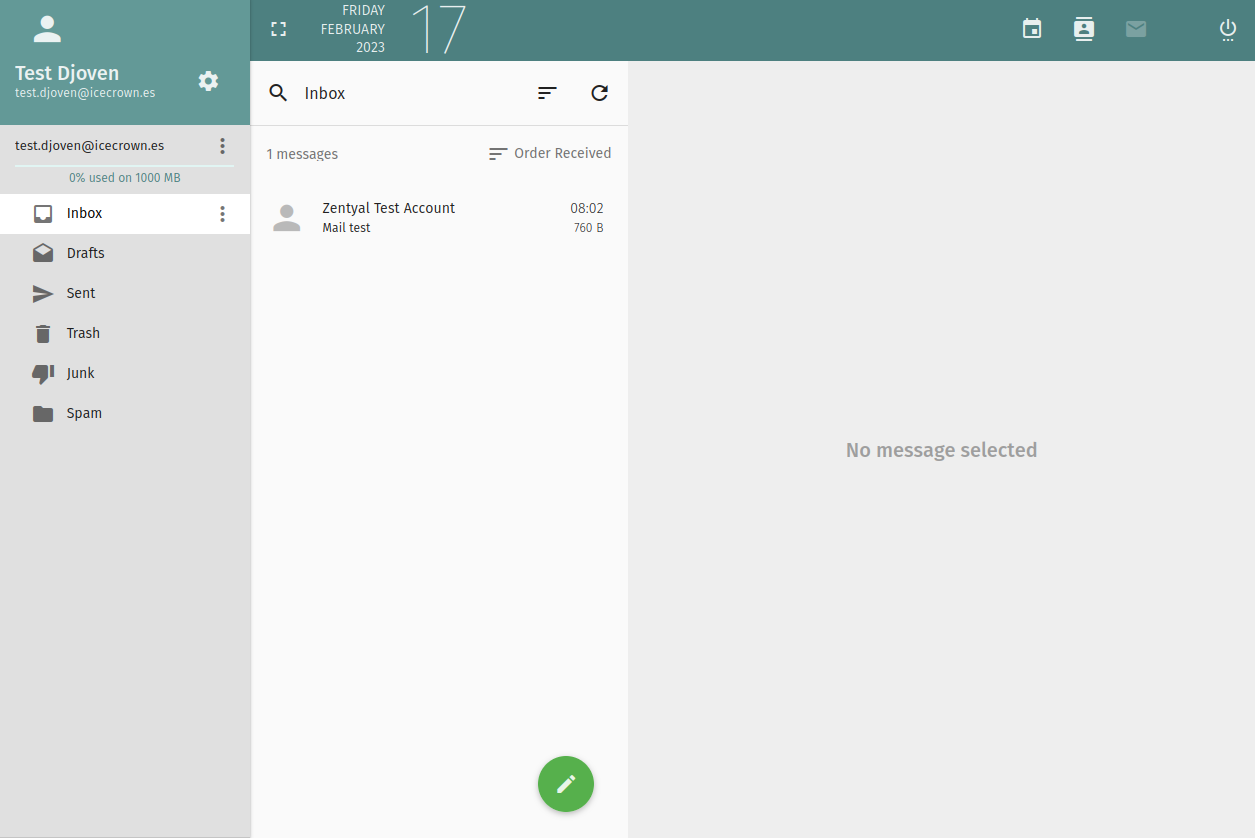
Once the security exception is confirmed, we should be able to see the email account:
-
Send a test email to ourselves and another to an external account to confirm the module's operation.
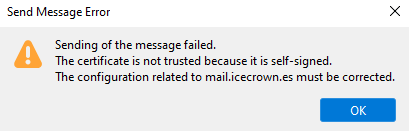
Nota
When we try to send the message, we will receive an error again due to the self-signed certificate, so we will have to confirm it again.
-
If everything went well, we should have received the email both internally and externally, and also in the
/var/log/mail.loglog we should see similar records as:Success
As can be seen, the status of both emails is
sent.
At this point, the mail module should be fully functional. However, it is not yet secured, so it is advisable not to use it yet until at least the Mailfilter module has been configured and enabled. Additionally, there is another page in this project called Hardening where the module's security will be further increased.
Also, note that if the server is installed in the AWS cloud provider, sending emails is not allowed by default (check the next to last section of the AWS page).
Webmail Module¶
The next module to configure will be the Webmail (Sogo), which will allow us to manage our email account from a web browser. Additionally, from the webmail, a user can change their password.
-
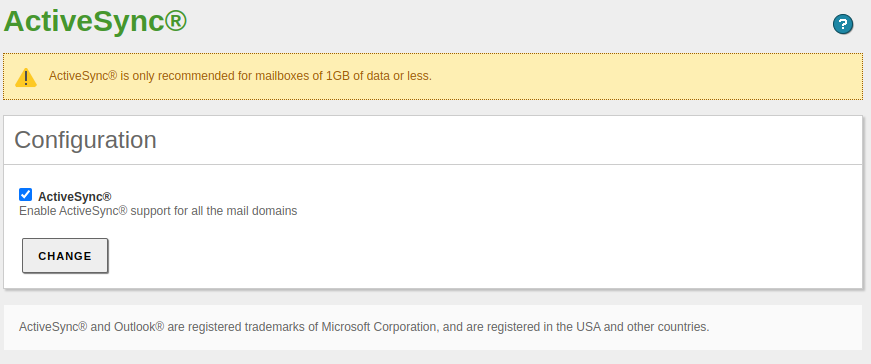
We enable the ActiveSync protocol from Mail -> ActiveSync in case users want to synchronize their mobile devices.
-
We enable the module.
-
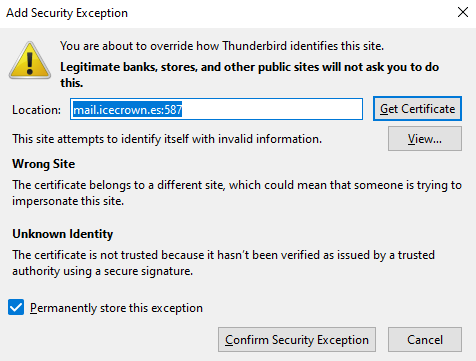
We check that we can access the login page from a web browser with the URL: https://arthas.icecrown.es/SOGo:
Warning
It will show a warning message due to the certificate used by the service, which is normal since it is self-signed.
-
Once we accept the exception, we should be able to see the login page:
-
We log in with the test user to confirm that authentication works correctly and that we can see our mailbox.
Warning
If we do not see the mailbox, it is possible that we are experiencing an existing bug, which occurs when the insecure mail protocols are not configured, and the certificate used is self-signed. To solve this, see the section
IMAPSon the bug fixing page. -
Finally, we try to send another email to ourselves to verify integration with the email module.
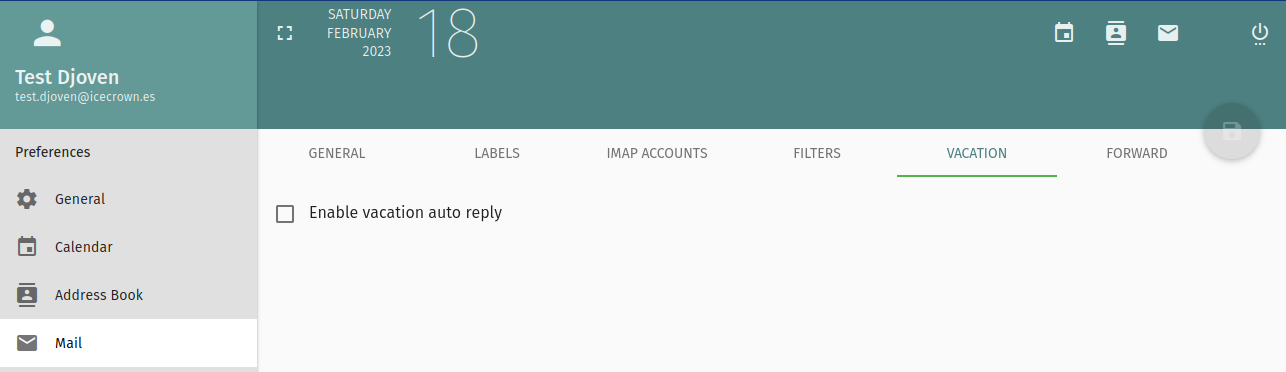
At this point, the module is fully functional; however, I will set the following optional configurations:
- I will enable the option of automatic messages for vacations since it is disabled by default.
- I will initially set the number of workers (processes) that the module will use to 8.
The following actions should be taken to apply the optional configurations:
-
We create the directory that will make the changes to the configuration templates (stubs) persistent against module updates.
-
We copy the Sogo configuration template
sogo.conf.mas. -
We set the parameter
SOGoVacationEnabledtoYESin the newly copied template. -
We restart the Webmail module to apply the change.
-
We log in to the Webadmin again and verify that the option is now available under
Preferences -> Mail. -
We set the value of prefork in the configuration file
/etc/zentyal/sogo.conf.If we have many concurrent users using the module, it is possible that Sogo cannot manage all requests properly, so it will be necessary to increase this value. To detect this scenario, we simply need to search for records in the Sogo log located at
/var/log/sogo/sogo.logsimilar to the following: -
We restart the Webmail module to apply the change.
-
Finally, we check that the service has been started with the new value applied.
In my case, the result obtained from the command was:
Antivirus Module¶
The next module we will configure is the Antivirus. Although this module consumes a lot of RAM, it is necessary for the analysis of the emails managed by the mailfilter module.
The configuration that we can define for this module from the Zentyal administration panel in the Development version is nonexistent. Therefore, we can only enable the module and verify that the signature database is up-to-date.
If using a commercial version, we will have the following additional functionalities described here:
- System analysis.
- Live monitoring of directories.
Mailfilter module¶
After enabling the Antivirus, we will proceed to configure the Mailfilter module, which will allow us to considerably increase the security of the organization's email service.
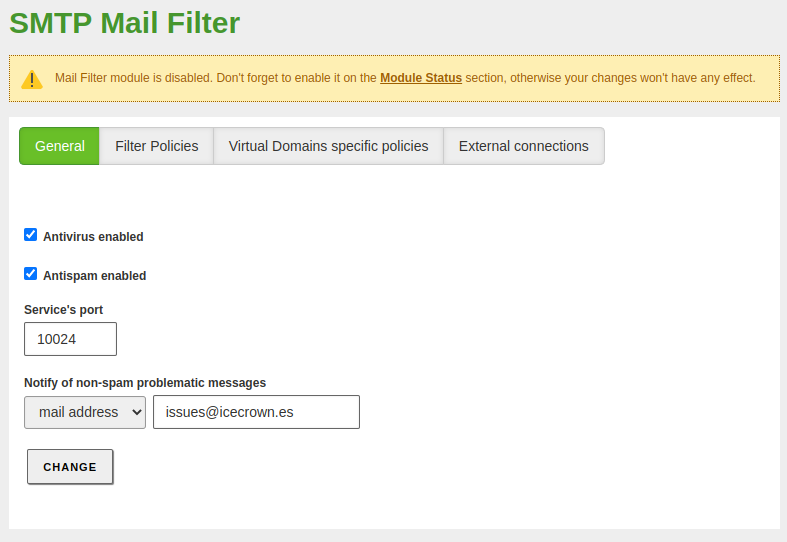
The configuration that I will apply will be:
- I will use the email account
issues@icecrown.esfor notifications of problematic emails. - I will set the threshold for emails considered as SPAM to 5.
- I will also set the auto-learn threshold to 5.
- I will add the domain to the whitelist.
- Except for the incorrect header policy, all other policies will be denied.
- I will disable certain extensions that can pose a security risk.
Here are the steps to configure the module:
-
We enable the services of this module and set an email address for non-spam problematic emails from
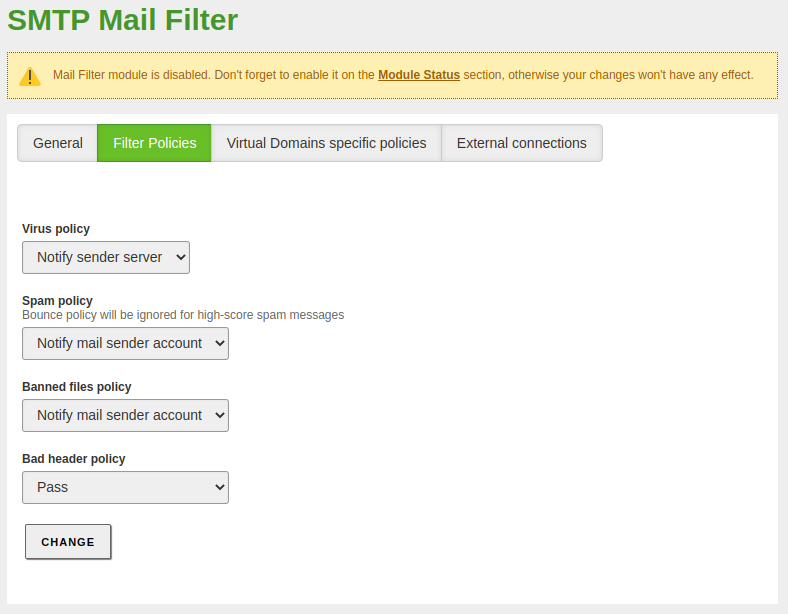
Mail filter -> SMTP Mail Filter: -
We set the default policies regarding the behavior of the module in response to certain events:
-
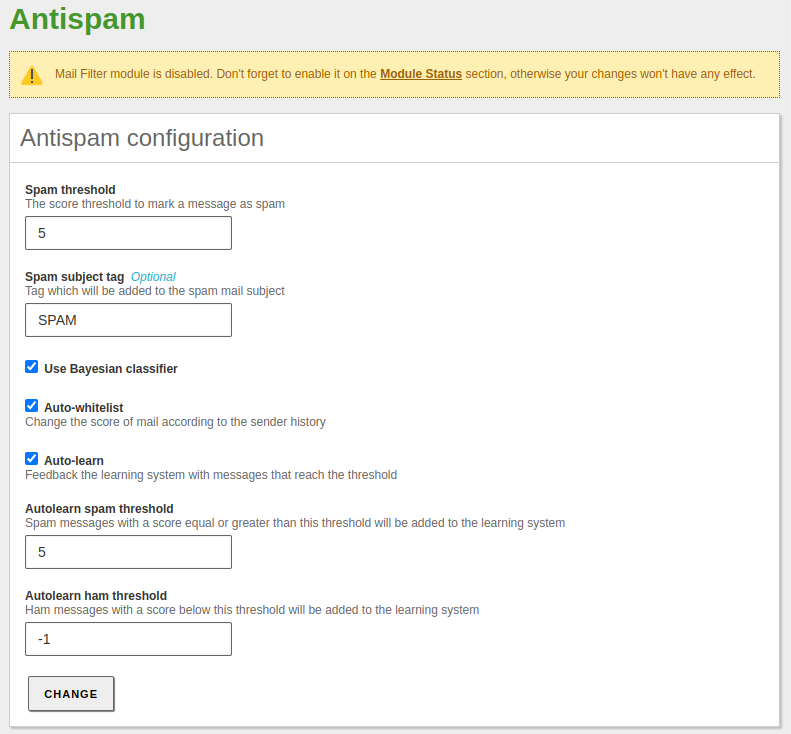
We set the antispam policies from
Mail Filter -> Antispam: -
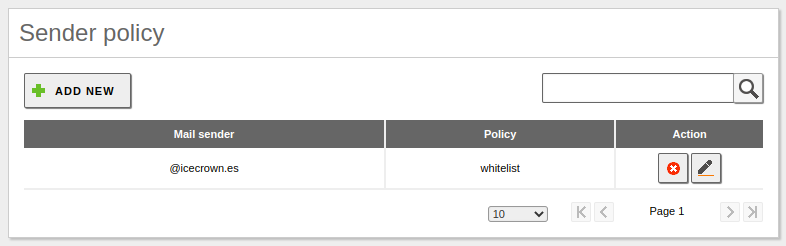
Optionally, we can add our domain to the whitelist so that it is not processed by the Mailfilter module:
-
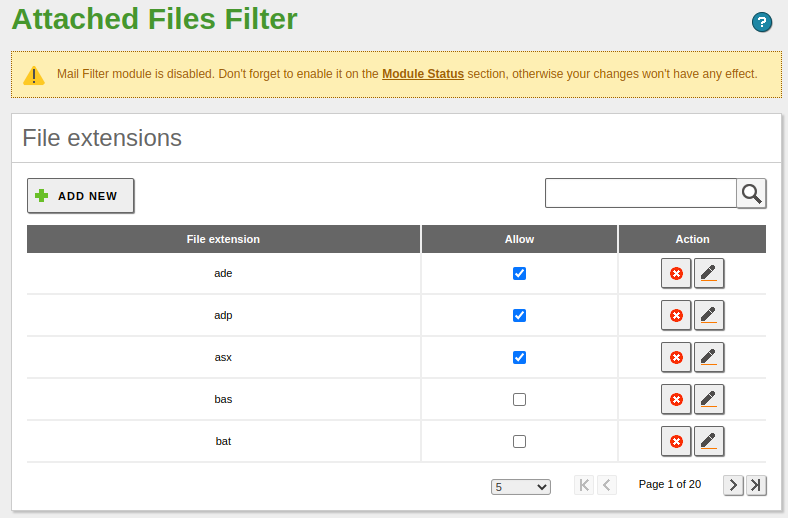
We disable the following extensions from
Mail Filter -> Files ACL -> File extensions:- bas
- bat
- cmd
- dll
- exe
- ini
- msi
- reg
- sh
-
We enable the module:
-
We create the email account that we established in step 1 from
Users and Computers -> Manage: -
We send a simple email from an external domain and check in the log file
/var/log/mail.logthat the module has analyzed it through the Amavis service:As you can see, the message arrived from a Gmail account, was analyzed by the 'Amavis' service, which scored it with '-5.947' and deemed it good, so the message arrived in the internal user's mailbox.
-
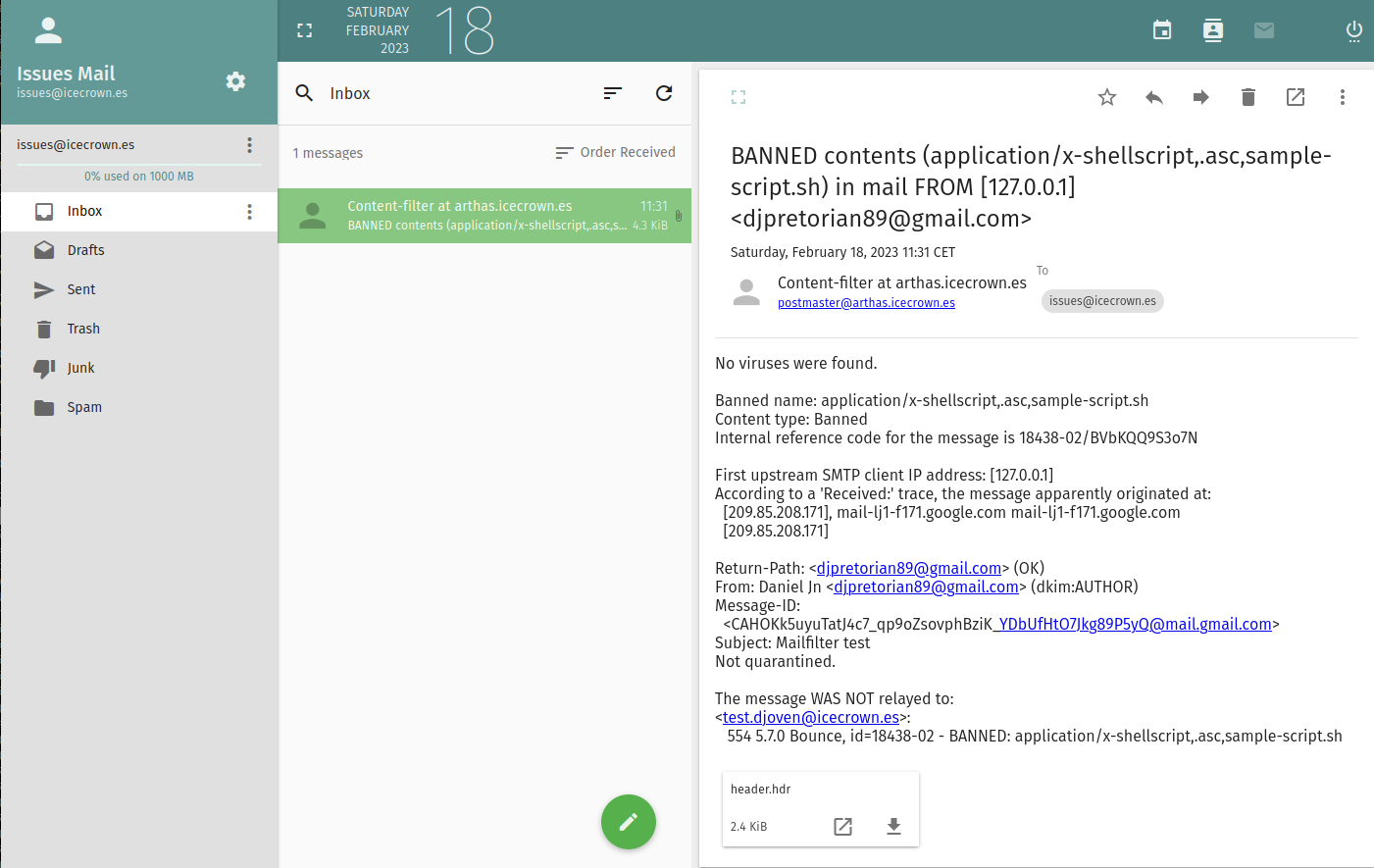
Once we confirm that emails are properly received, we will proceed to verify the functioning of the module by sending another email with an attachment whose extension is
.sh- denied in step 5 - from an external account. Here are the log records regarding the success of the block in/var/log/mail.log:As can be seen, the email from a GMail account arrived at the server, the Amavis service analyzed it and denied it due to the extension of the attached file. Then it notified
issues@icecrown.esand finally returned the email to the external account. -
Finally, we confirm that the
issues@icecrown.esaccount has an email with our latest test.
At this point, our email service is secure enough to be used in production. However, it is highly recommended to configure at least SPF and DKIM, and ideally, DMARC. These security configurations are discussed on the Hardening page. Additionally, it is also recommended to establish certificates issued by recognized certification authorities such as Let's Encrypt. Again, this will be addressed on another page of the project, specifically in Certificates.
CA module¶
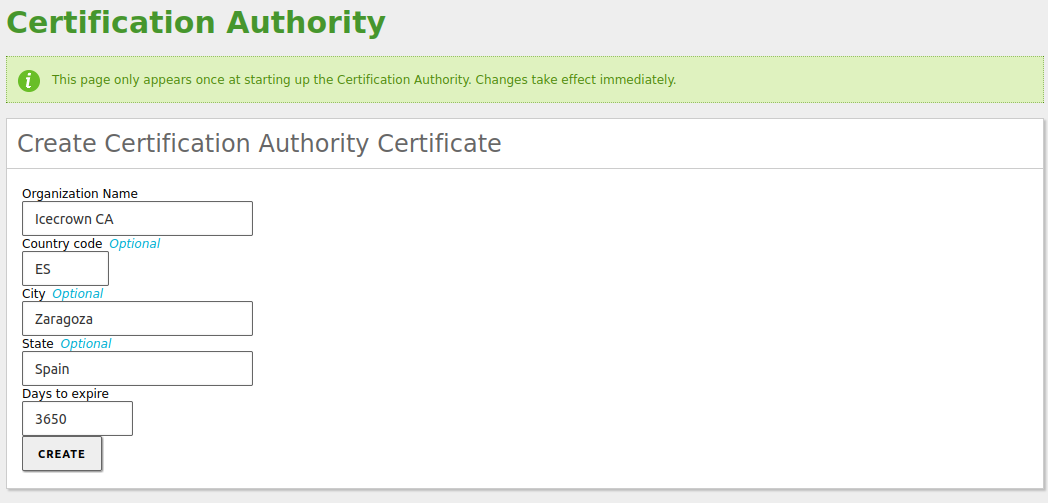
In order to use the OpenVPN module, we need to configure the CA module beforehand, which is extremely easy to set up.
-
We create our certification entity from
Certificate Authority -> General: -
Finally, we save changes for our CA to be created.
Info
This module cannot be 'enabled' like the others.
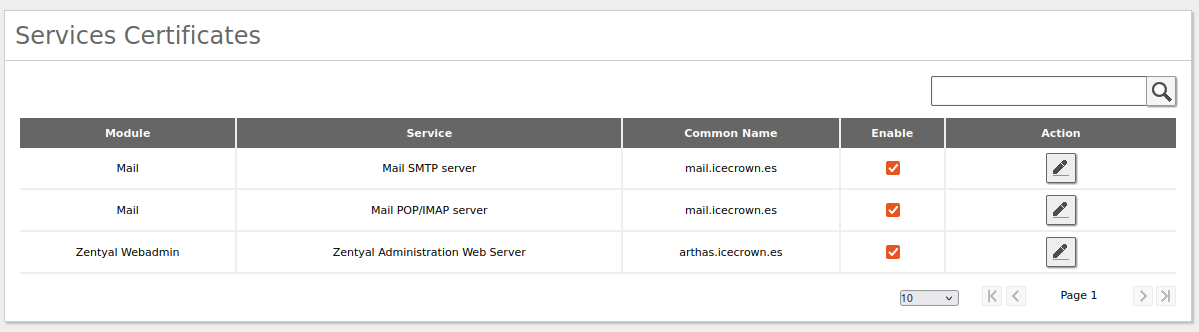
Additionally, it is possible to issue certificates for the modules we are using with the correct CommonName, however, since we are going to issue certificates recognized through Let's Encrypt, we will not use such functionality. If you want to use it, you would have to go to Certificate Authority -> Services as indicated below:
OpenVPN Module¶
The last module we will configure will be OpenVPN. The purpose of using this module is to allow domain users to securely access the shared resources configured in the domain controller module from any location.
The settings I will establish are:
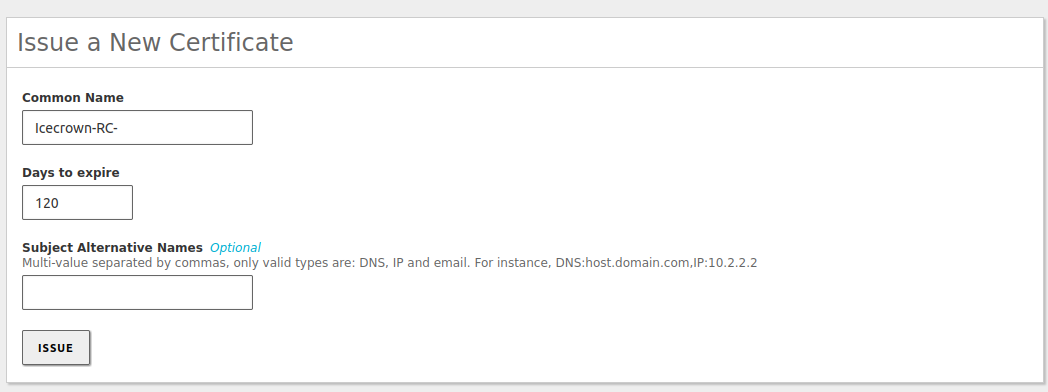
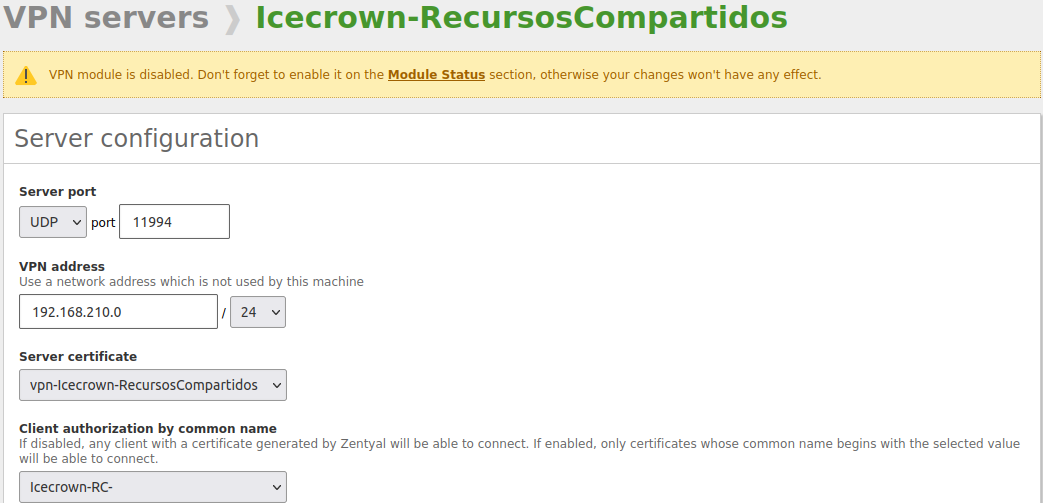
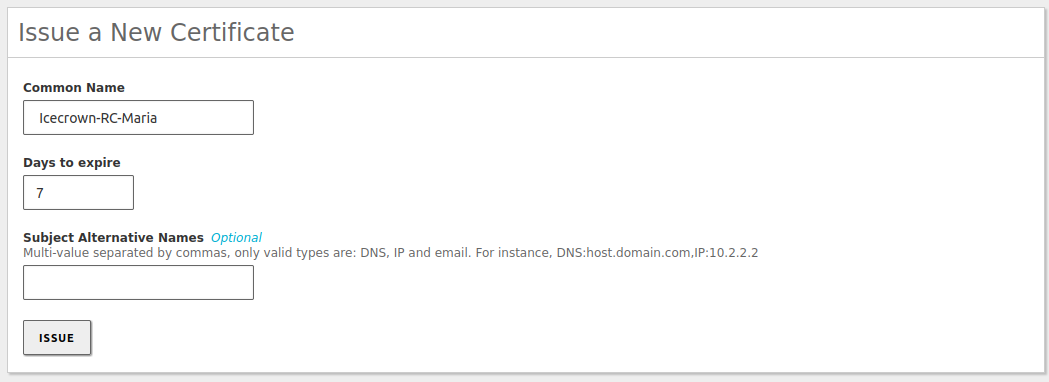
- As an additional security measure, access will only be allowed using certificates with the CommonName prefix: Icecrown-RC-.
- The VPN connection prefix certificate will have a validity of 120 days. However, it should be noted that setting this value will force us to perform maintenance tasks every 4 months.
- A different VPN port and address than the default will be used.
The following steps need to be performed to configure the module:
-
Create the certificate that we will use as the name. To do this, go to
Certificate Authority -> General: -
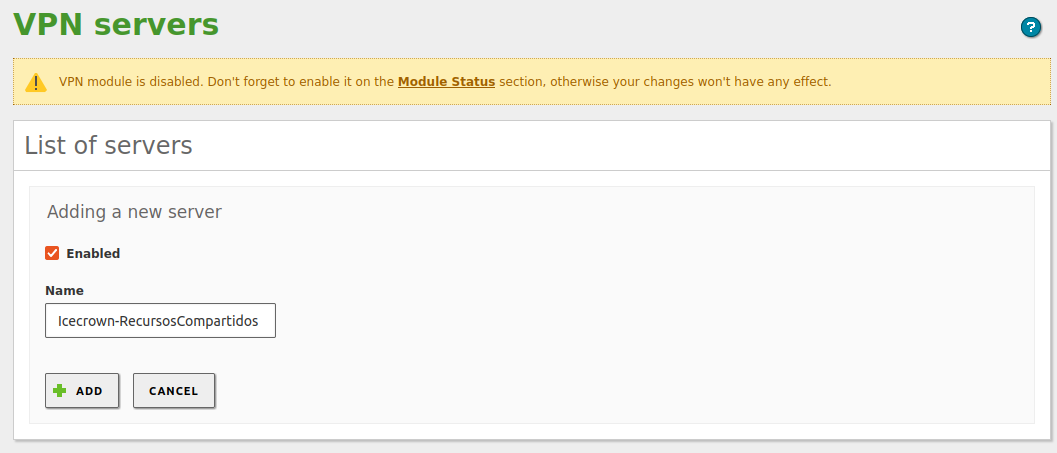
Create the VPN connection from
VPN -> Servers: -
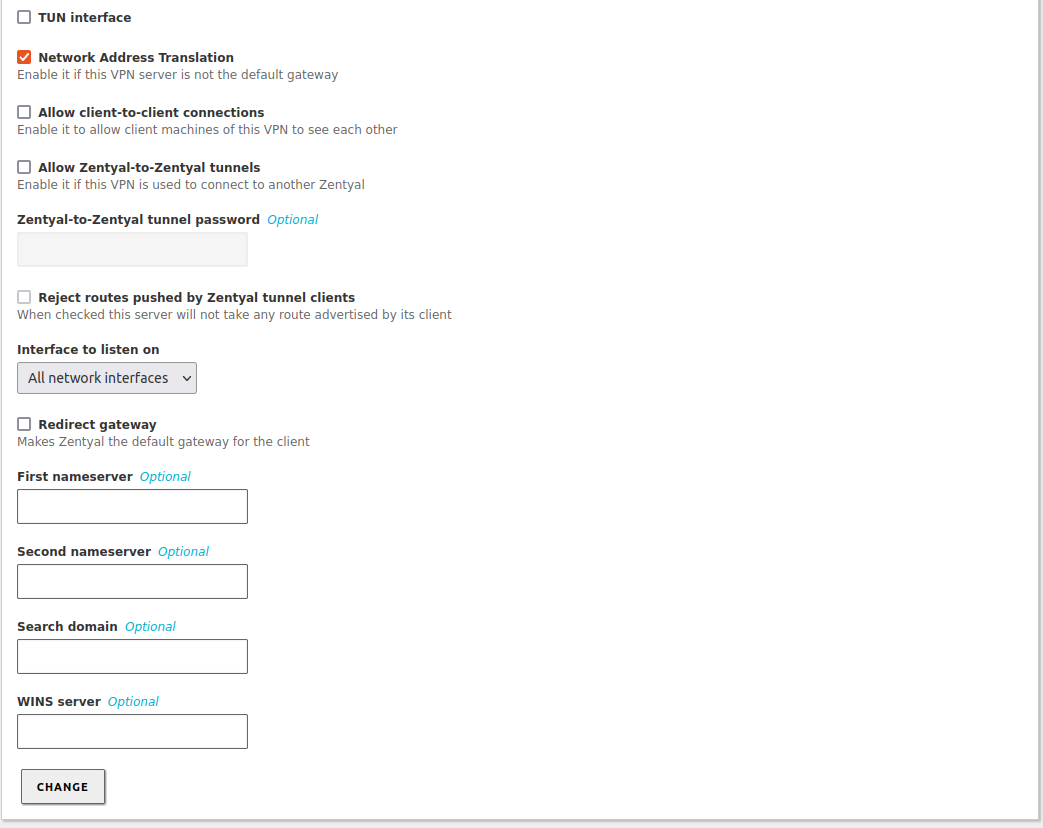
Configure the connection from
VPN -> Servers -> Configuration: -
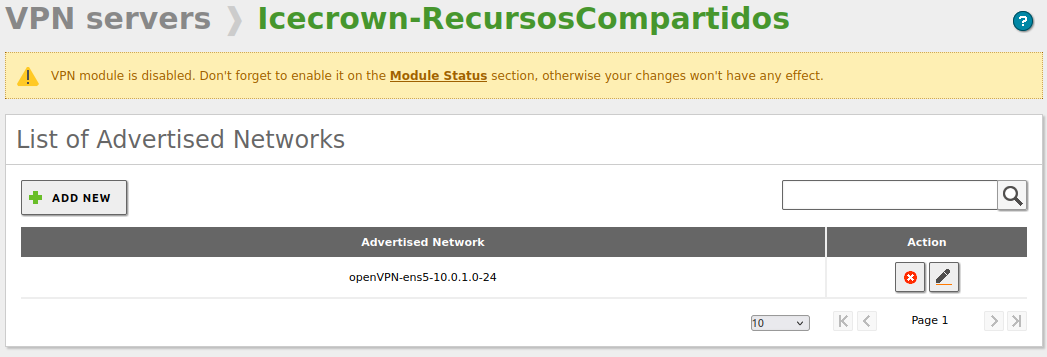
Confirm that the server's internal network is configured in the VPN connection by going to
VPN -> Servers -> Advertised networks: -
Enable the module:
-
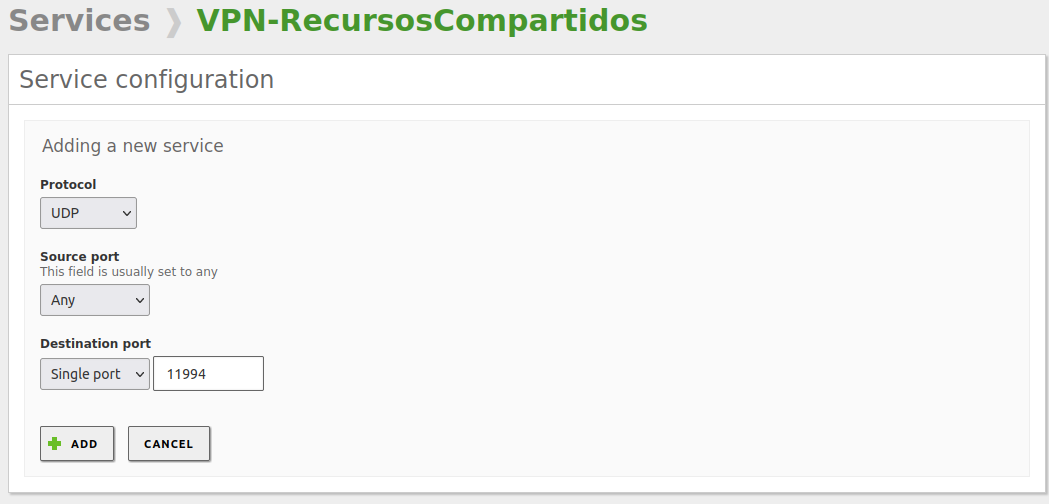
Create a network service with the defined VPN connection port:
Warning
Remember that the protocol is UDP.
-
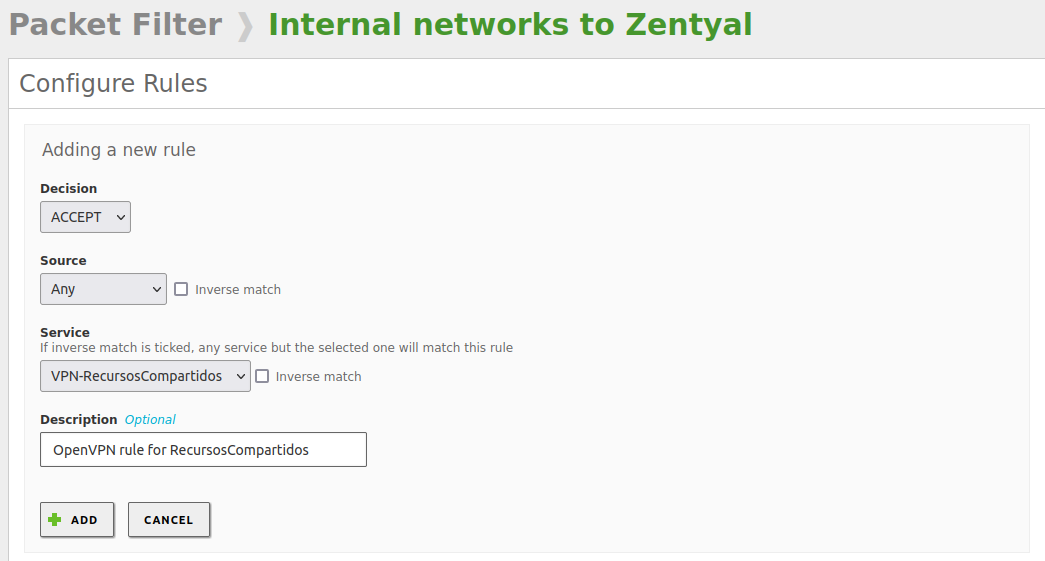
Finally, create a rule in the Zentyal firewall that allows the connection and save changes:
With the module now configured, we create a certificate, user, and shared resource to confirm the full functionality of this module. To do so, follow these steps:
-
Create a certificate:
-
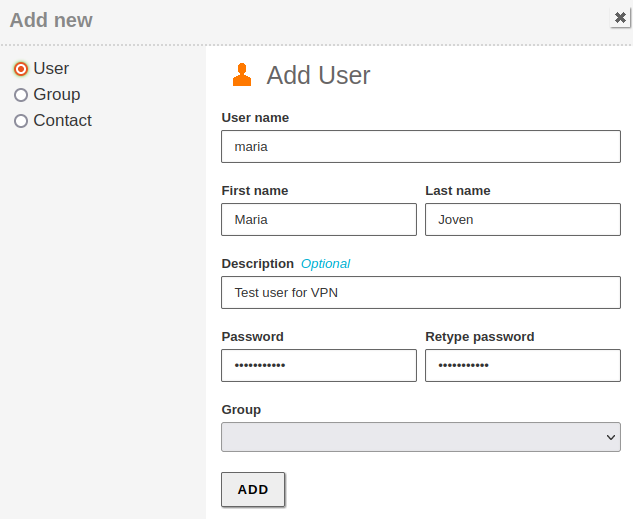
Create a domain user:
-
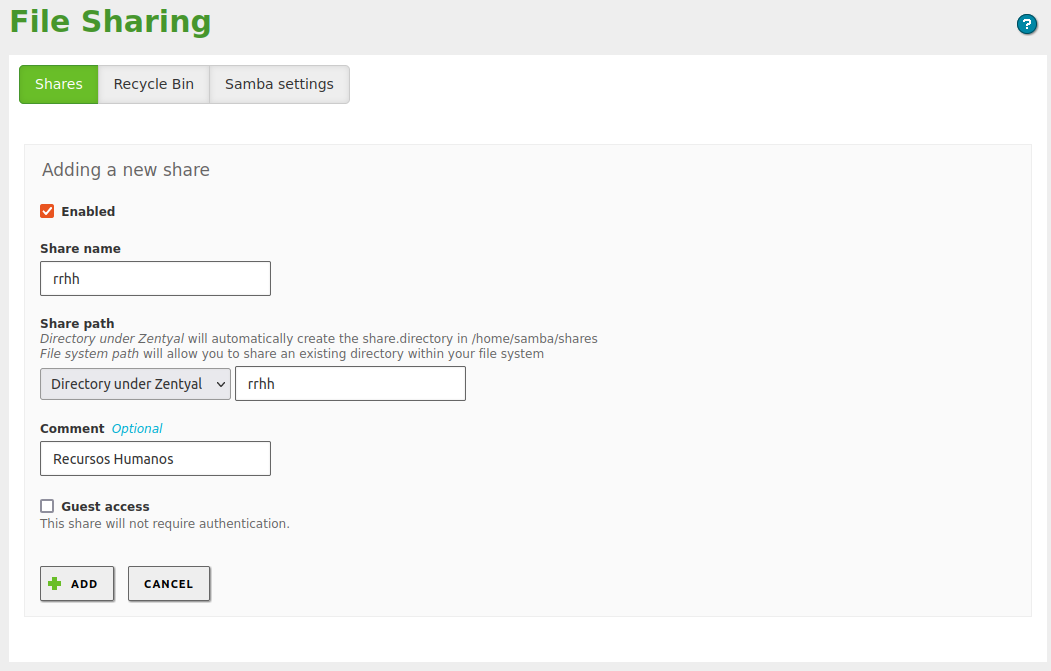
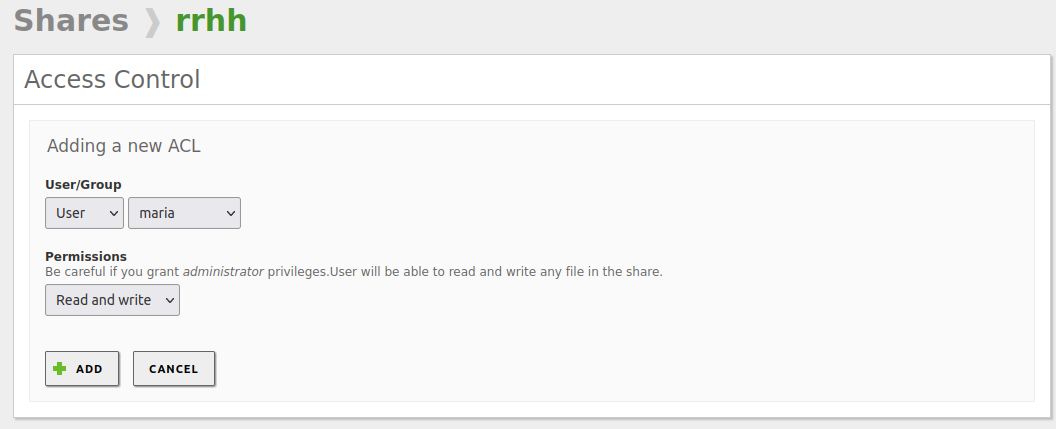
Create a shared folder with read and write permissions for the test user:
-
Save changes.
-
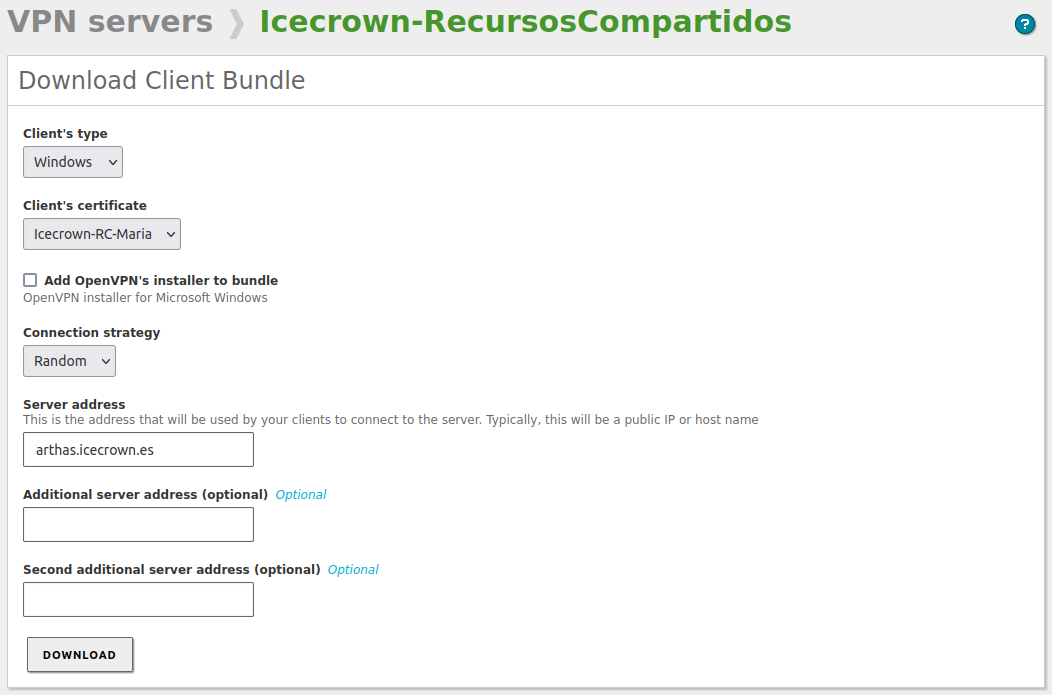
Download a bundle with the VPN connection configuration for the client by going to
VPN -> Servers -> Download client bundle:Note
For this specific example, I will use a Windows 10 machine with OpenVPN already installed for the client.
-
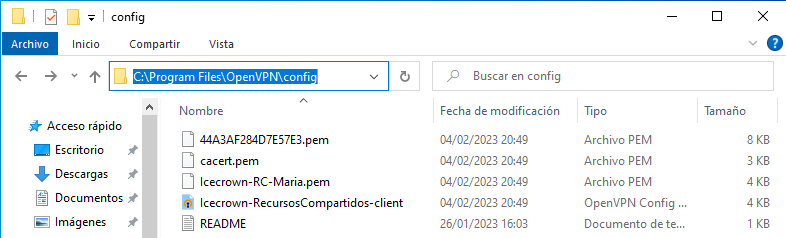
Copy the bundle to the client from where you want to establish the VPN connection and configure the OpenVPN client:
-
Establish the connection from the OpenVPN client. If everything went well, we should be able to see similar logs in the Zentyal VPN connection log file called
/var/log/openvpn/Icecrown-RecursosCompartidos.log: -
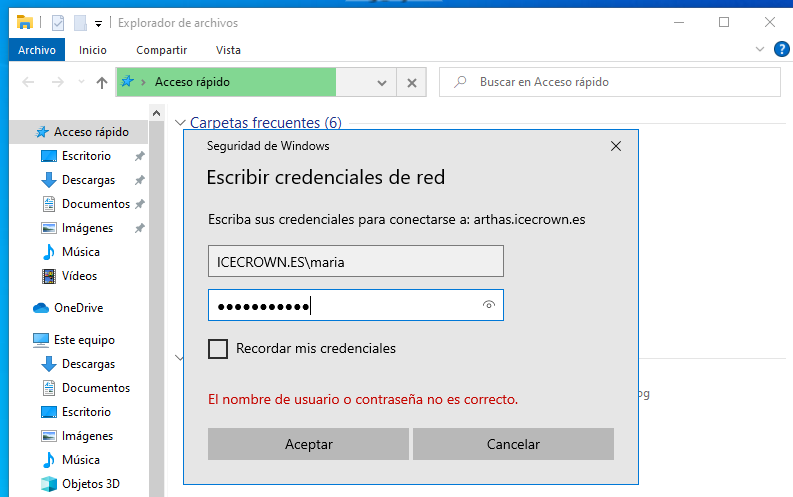
Once the connection is established, from the file browser, we will set the server URL, which in my case is:
\\arthas.icecrown.es. Then, it will ask us for the user credentials. -
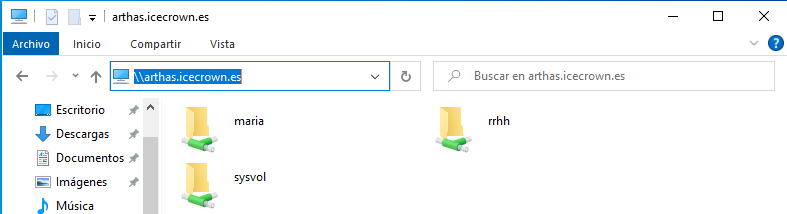
After logging in, we should see the user's personal directory and shared resources.
-
Add a file to the
Mariaandrrhhresources and verify its creation from the Zentyal server CLI:
At this point, the server would be ready for production use. However, as mentioned several times, it is highly recommended to perform certain additional tasks such as:
- Use certificates issued by recognized certification authorities.
- Secure the email service with SPF, DKIM, and DMARC.
- Set restrictions on domain user passwords.
- Create a backup policy.
- Monitor the server.
- Know and schedule maintenance tasks.
All these configurations will be explained on other pages of the project (see top menu).
Created: April 12, 2023